Windows Exploit Development Megaprimer
Learn how to write reliable exploits.

What you will learn
Learn how Exploit Works
Bypass memory protections
Make exploits reliable
Scenario based Exploit Development
Port Exploits into Metasploit modules
Why take this course?
This is a comprehensive course on Exploit Development in Windows platform. The course is designed in such a way to help the beginners. It will help you understand the different domains of software exploitation.
The participants will learn about different types and techniques of exploitation, using debuggers to create their own exploits, understand protection mechanism of the Operating Systems and how to bypass them. You will also learn how to write and execute an exploit in the latest Windows operating systems like Windows 7 and 8. This course will be supported by additional reference materials that will help you to understand the concepts and for further reading. The the course content will be updated regularly.
What you will learn?
- Learn stack based buffer overflow
- Exploiting buffer overflows
- Understand and write shellcodes
- Write exploits for Win32 platform
- Bypassing various memory protections
- Making your exploits reliable
- Write remote and local exploits
- Converting your exploits to metasploit modules
- Learn about concepts like Vanilla EIP Overwrite, Egg hunting, SEH overwrite, ROP chains etc.
- Learn to use various exploit development tools like debuggers, mona extension etc.
Who should attend this course?
- Pentesters
- Network/system administrators
- Reverse engineers
- Malware analysts
- Security enthusiasts
- Anyone interested in exploit development.
What are the Prerequisites?
- Working knowledge of Windows and Linux Operating Systems
- Knowledge in scripting languages like Python, Perl or Ruby
- Comfortable with command-line utilities
- Basics of Assembly language
Why take this course ?
- Do you want to learn how to read and understand existing exploits?
- Do need to successfully modify an existing exploit?.
- Do you want to write reliable exploits and port them into Metasploit modules?
- Do you want to know how shellcode works ?
- Do you need to understand the basic concepts of exploit writing?
- Are you willing to dig deeper into shellcodes and debugger?
- Then this course is for you!
Reviews
Charts
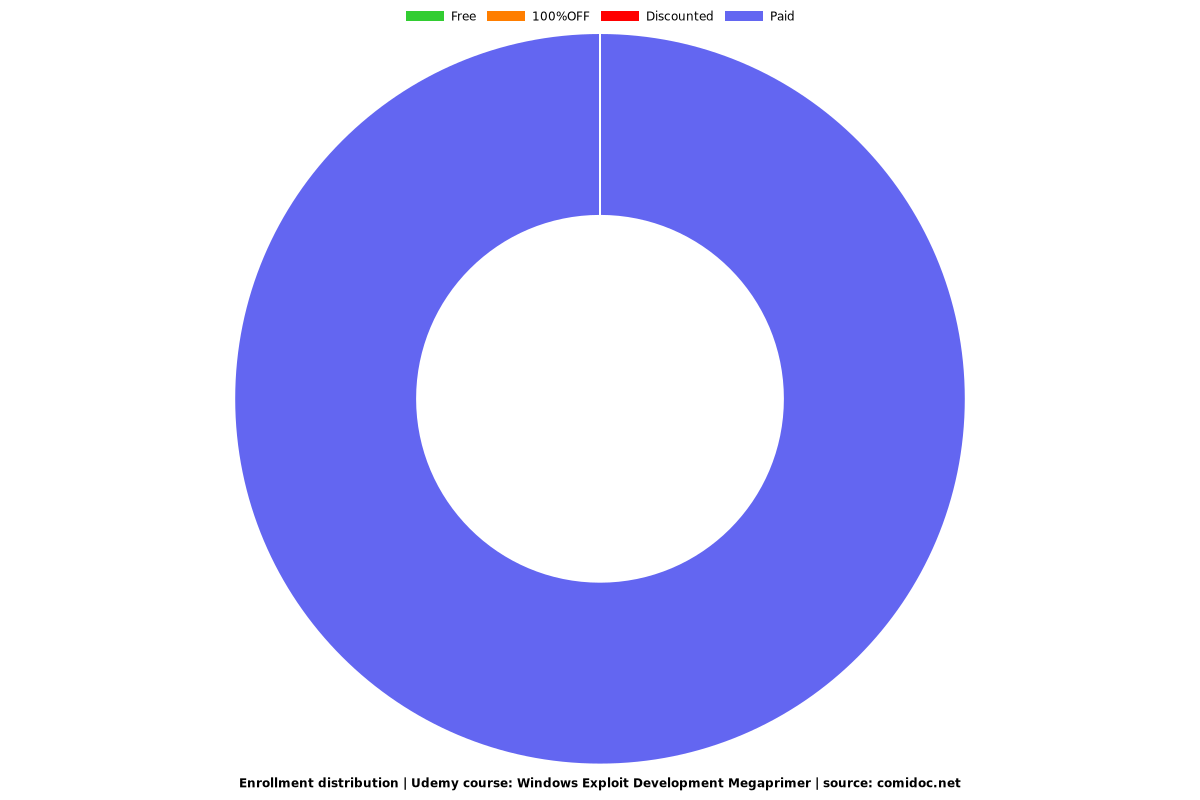
Price
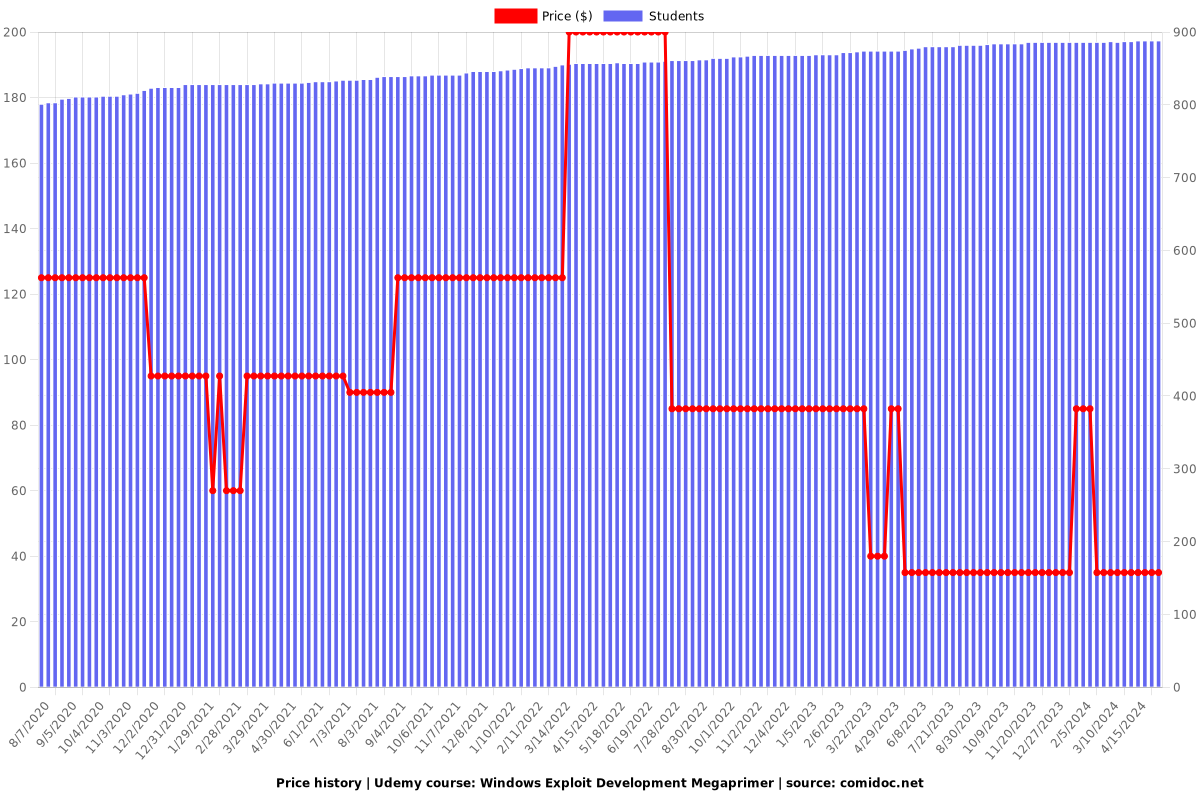
Rating
Enrollment distribution