Ultimate Bug Bounty
Learn the art of finding and automating the bugs

What you will learn
Web Fundamentals
Python Fundamentals
Automating Bug Hunting with Python
Different WebApp Vulnerabilities
Burp Suite Fundamentals
Injection Vulnerabilities
File Inclusion Vulnerabilities
OWASP TOP 10
Why take this course?
This course teaches you how to find bugs in web applications . This course also teaches you Python and also covers most of modules in automating with python . Having Programming skills became necessary in rapidly growing industry . Same applies to cybersecurity and bug hunting . Python helps in automating many things and saves you a ton of time . This course also covers OWASP Top 10 Vulnerabilities . This course can be a good starting point for your bug bounty journey . More and more content will be added from time to time just like my other courses . Modules upto Python Fundamentals were recorded year ago so they contain my bad english but from then onwards there will be no problem in watching videos .
This paragraph tells you essence of cybersecurity
Use of cyberspace, i.e. computer, internet, cellphone, other technical devices, etc., to commit a crime by an individual or organized group is called cyber-crime. Cyber attackers use numerous software and codes in cyberspace to commit cybercrime. They exploit the weaknesses in the software and hardware design through the use of malware. Hacking is a common way of piercing the defenses of protected computer systems and interfering with their functioning. Identity theft is also common. Cybercrimes may occur directly i.e, targeting the computers directly by spreading computer viruses. Other forms include DoS attack. It is an attempt to make a machine or network resource unavailable to its intended users. It suspends services of a host connected to the internet which may be temporary or permanent.
Malware is a software used to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It usually appears in the form of code, scripts, active content, and other software. ‘Malware’ refers to a variety of forms of hostile or intrusive software, for example, Trojan Horses, rootkits, worms, adware, etc.
Reviews
Charts
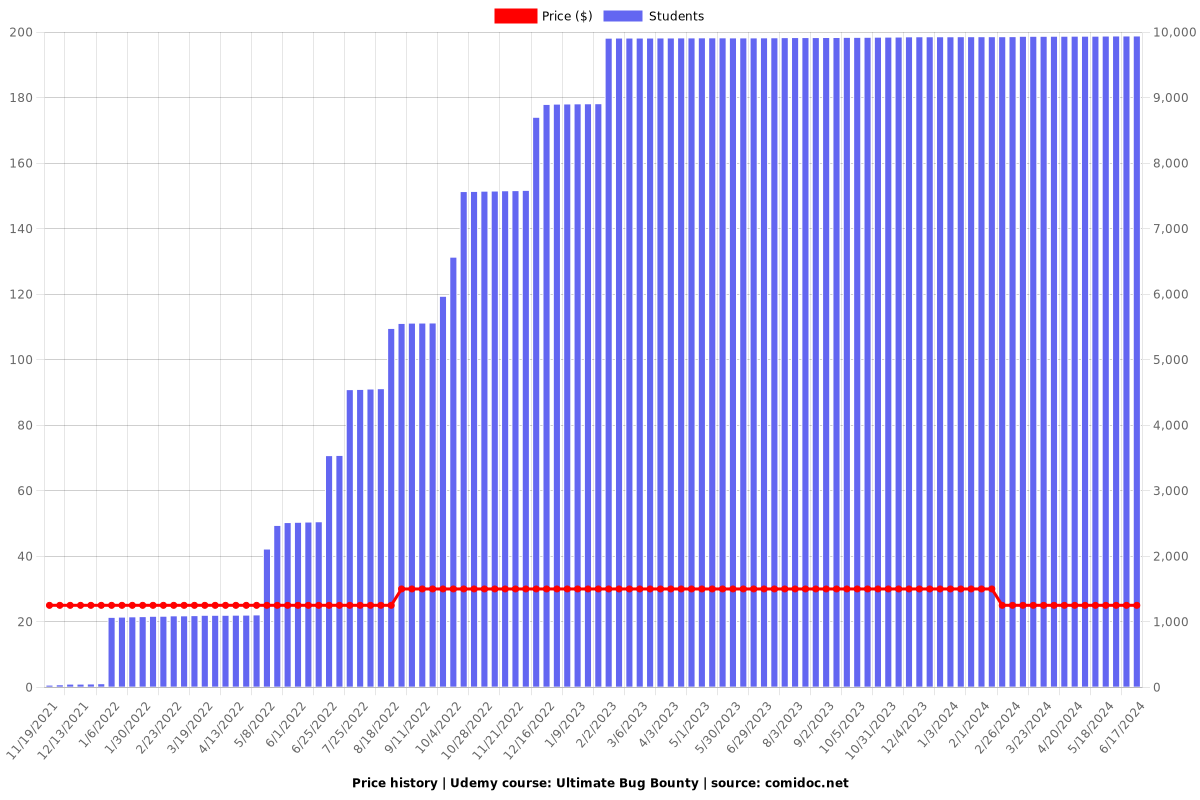
Price
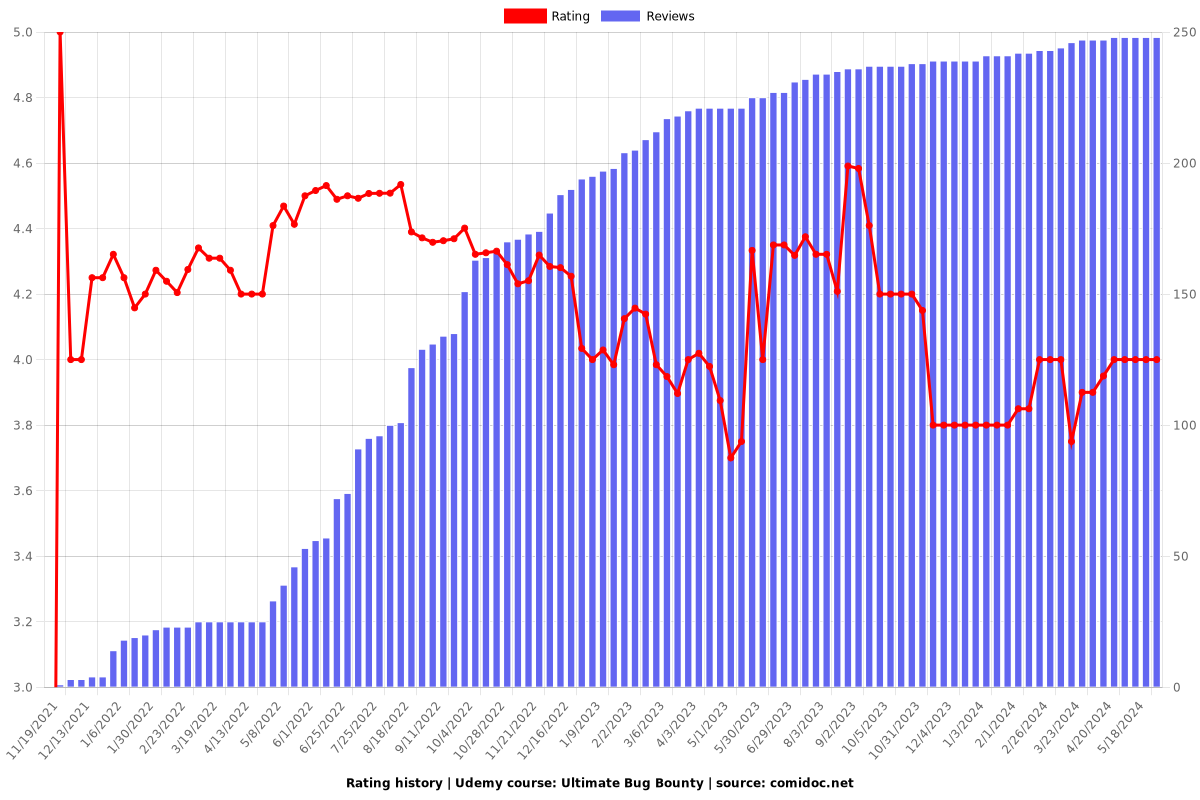
Rating
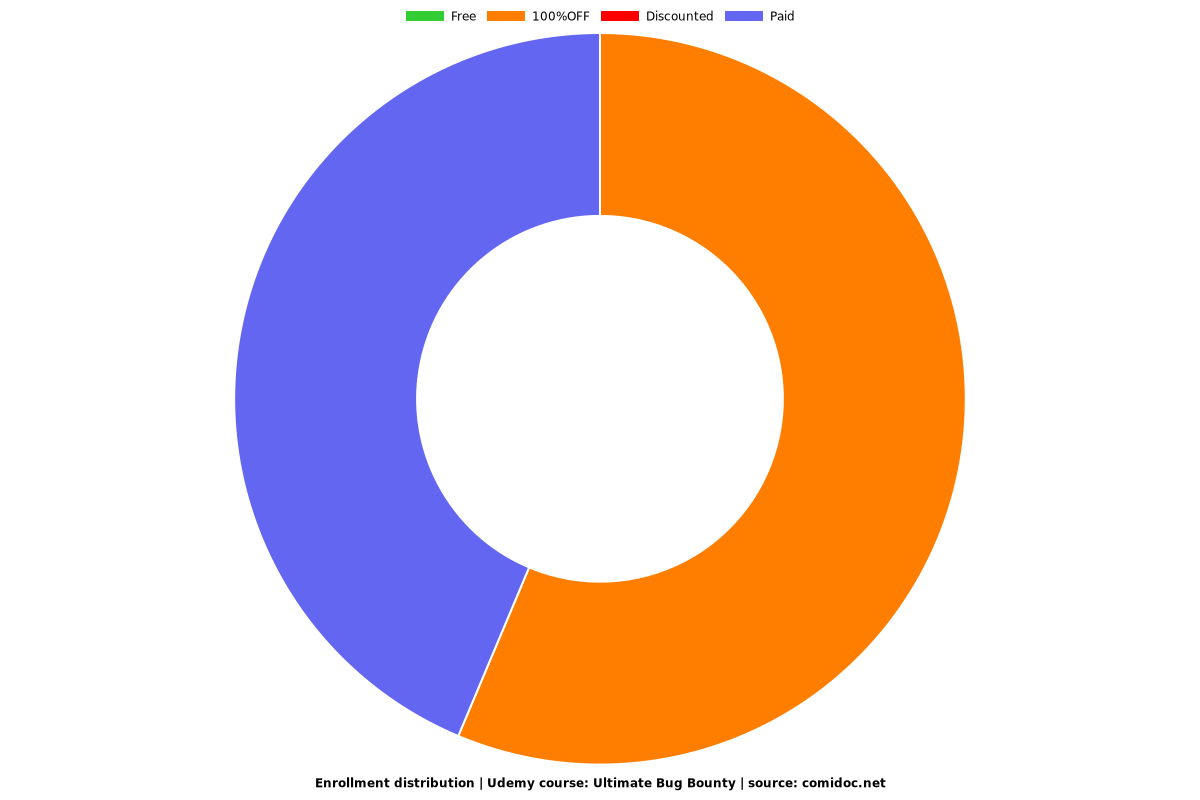
Enrollment distribution