Title
NEW-The Complete Ethical Hacking Boot camp-From Zero to Hero
A Comprehensive Beginner's Guide To Learn And Master Ethical Hacking!

What you will learn
70+ ethical hacking & security videos.
Start from a beginner up to a high-intermediate level.
Learn what is ethical hacking, its fields and the different types of hackers.
Install hacking lab & needed software (works on Windows, MAC OS X and Linux).
The ability to secure and protect any network from hackers and loss of data.
Discover vulnerabilities & exploit them hack into servers.
More than 35+ hacking tools such as Metasploit,sAINT spyware,Beelogger,SQL Map.....and more
Tips for remaining anonymous in hacking and penetration testing activities.
Secure systems from all the attacks shown.
Install Kali Linux -the best penetration testing OS (Hackers Love this OS).
Learn linux basics.
Learn Linux commands and how to get really comfortable with it:)
Learn Network Penetration Testing.
Crack WEP/WPA/WPA2 encryptions using a number of methods.
Sniff packets from clients and analyse them to extract important info such as: passwords, cookies, urls, videos, images ..etc.
Discover open ports, installed services and vulnerabilities on computer systems.
Take a look at SHODAN-Search Engine.
What SHODAN search engine is and how to use it effectively.
Install (s)AINT Spyware in kali linux and start spying any system(Webcamsnaps,Keylogger,Persistence)
Install and configure Beelogger in kali linux and start getting keylogs from the victim
Create undetectable backdoors(FUDs)
Use social engineering to gain full control over target systems.
Capture keystrokes on a compromised system.
Gather sensitive information about websites(SQL INJECTION).
Discover, fix, and exploit SQL injection vulnerabilities.
Bypass login forms and login as admin using SQL injections.
You'll learn what is WIRESHARK is.
Start sniffing data around using WIRESHARK and gather information.
A brief overview on what VPNs are how do they work.
Get added to telegram hacking groups and start valuable information from them.
How to Install TAILS OS and start using it right from now to protect against somr one spying you
What is TOR and how to install it on any OS(Windows,OS X,Linux) and how to use it to access the hidden sites on deep web.
Use TOR Anonymous Chat Rooms and Learn how do they work.
Explore the - Darknets, dark markets, zero day vulnerabilities, exploit kits, malware, phishing and much more.
And Finally i will be updating the course frequently with the latest hacking methods and cool computer tips and tricks.....
Why take this course?
🚀 Course Headline: A Comprehensive Beginner's Guide To Learn And Master Ethical Hacking!
🎉 Course Description:
Are you ready to dive into the world of cybersecurity and emerge as a bonafide ethical hacker? Whether you're aspiring to kickstart your career in IT, enhance your network security knowledge, or simply satisfy your curiosity about the digital frontier, "NEW-The Complete Ethical Hacking Bootcamp - From Zero to Hero" is your ultimate guide!
🎓 What You'll Learn:
- Introduction to Ethical Hacking: Understand the basics and what it means to be an ethical hacker. 🛡️
- Hacking Terminology: Get acquainted with essential terms and concepts in the field of cybersecurity. 📚
- Setting Up Your Hacking Lab: Learn how to create a secure environment for your ethical hacking experiments. 🖥️
- Virtual Machine Installation: Master the installation of VMware and Virtual Box on various operating systems like Windows, MAC OS X, and Linux. 💻
- Linux Terminal Skills: Gain proficiency in the Linux Terminal and Command Line Interface (CLI) for effective navigation and control. 🐧
- Anonymity Tools: Explore the Tor Browser, ProxyChains, and other tools to enhance your online anonymity. 🌐
- VPNs & Anonymous Surfing: Discover how VPNs work and how you can stay securely anonymous online with tools like Anonym8 and Anonsurf. 🔒
- WiFi Cracking: Learn to crack WEP/WPA/WPA2/WPS Pins and gain unauthorized access to WiFi networks. 📶
- System Hacking & Exploitation: Gain full control over Windows and iOS systems using Metasploit and identify vulnerabilities. 🛠️
- Mobile Hacking: Understand how to hack into Android and Apple (iOS) mobile devices. 📱
- Encryption & More: Get a crash course on encryption and much more! 🔑
📺 Course Features:
- Lifetime access to over 14+ hours of HD video tutorials. 🎥
- A hands-on approach to learning ethical hacking through practical exercises.
- Personal guidance from the course instructor, Ramsai Dupati, throughout your learning journey. 🤝
- A vibrant Q&A community where you can ask questions and receive prompt assistance. 💬
- Monthly updates to ensure the course content stays current with the latest hacking methods and techniques. 🚀
📈 Disclaimer & Certification:
- This course demonstrates attacks for educational purposes only. It is crucial to use this knowledge responsibly. ✊
- Upon completion, you will receive a Course Completion Certificate from Udemy. 🏆
- Please note that this course is exclusively created by Ramsai Dupati and is not affiliated with any other organization. 🌐
What You Get:
- 15+ hours of on-demand video content with English subtitles. 📺
- Full lifetime access to course materials. 📚
- Accessible on mobile and TV devices for learning anytime, anywhere. 📱📺
- 24/7 support for any questions or concerns during your course experience. ☎️
🎉 Join the Community of Ethical Hackers!
Embark on your ethical hacking journey with "NEW-The Complete Ethical Hacking Bootcamp - From Zero to Hero" and transform your understanding of cybersecurity. With Ramsai Dupati's expert guidance, you'll be well-equipped to tackle the challenges of network security and beyond! 🛡️💻
Thank you for considering this course, and we can't wait to see you on the inside, where your cybersecurity adventure awaits! 🚀🔐
Screenshots




Our review
Course Review for Ethical Hacking
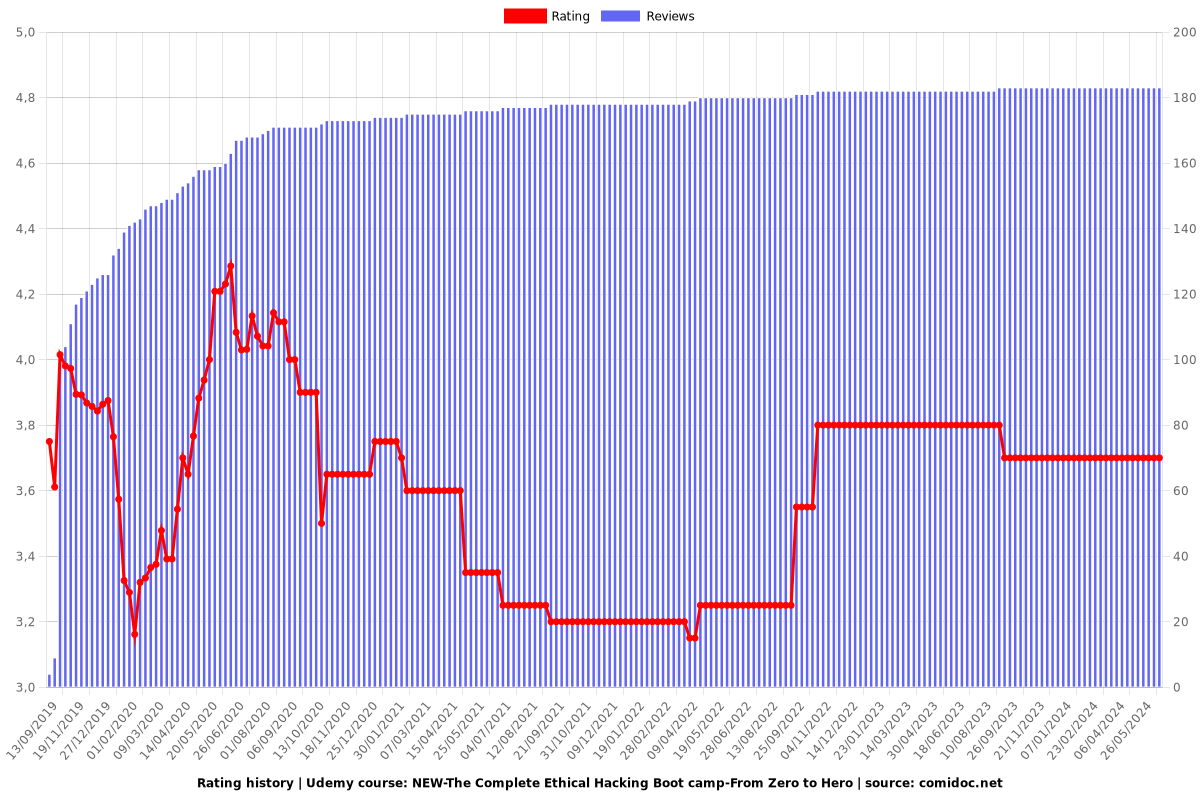
Overall Rating: 3.70
Pros:
- Comprehensive Content: The course covers a wide range of topics within the field of ethical hacking and provides a good overview.
- Large Volume of Videos: There is an abundance of video content, which can be beneficial for learners who prefer visual learning and those looking to get exposed to various aspects of the subject.
- Insightful for Young Learners: The course was found to be insightful even for a 14-year-old, suggesting its potential to inspire and contribute to young individuals' careers in computers and cybersecurity.
- Positive Feedback: Some users reported that the course content was good and interesting, helping them explore new interests in ethical hacking.
- Knowledge Sharing: The instructor was commended for sharing deep knowledge about the subject and for presenting the information clearly.
- Practical Examples: One user appreciated the practical examples provided, which were considered better than those in other courses.
- Course Usefulness: Some learners found the course useful and helpful for acquiring new skills.
Cons:
- Technical Errors: Several users pointed out numerous errors made by the instructor during video explanations, which could be both distracting and misleading.
- Pacing Issues: The teaching pace was described as slow, with some learners feeling that the content could be condensed to eliminate unnecessary parts and avoid watching mistakes repeatedly.
- Repetition and Confusion: Some users found the instruction confusing due to repetitive explanations or mixed methods for performing the same process.
- Audio Clarity: One learner had difficulty understanding the voice clarity in one of the videos, suggesting the need for subtitles for non-native speakers.
- Outdated Content: Concerns were raised about the course content being outdated, particularly in the section on Android hacking, indicating a need for updates to reflect current methodologies.
- Language Proficiency: There were suggestions that if the instructor was not comfortable with English, using another language like Hindi might be more effective, or improving the English grammar to enhance clarity.
Additional Feedback:
- Course Length: Some users felt that the course could be shortened by eliminating unnecessary content, such as a tutorial on downloading DVWA if it's not used further.
- Introductory Concerns: One user noted that the introductory material appeared to be taken from another source, raising questions about originality and copyright issues.
- Request for Updates: A learner requested an update to the course content specifically for the Android hacking section to include the latest techniques involving images.
Conclusion: The Ethical Hacking course has its strengths in terms of comprehensive coverage and the clarity with which knowledge is shared, but it also faces challenges related to technical errors, pacing issues, and the need for content updates. Learners are encouraged to utilize this course as a starting point, especially if they can access it for free or consider it within their budget, while keeping in mind that an experienced instructor might offer more advanced and less error-prone learning experiences. For beginners, this course could serve as an introduction to ethical hacking, with the caveat that learners should complement the instruction with additional resources to fill in any gaps.
Charts
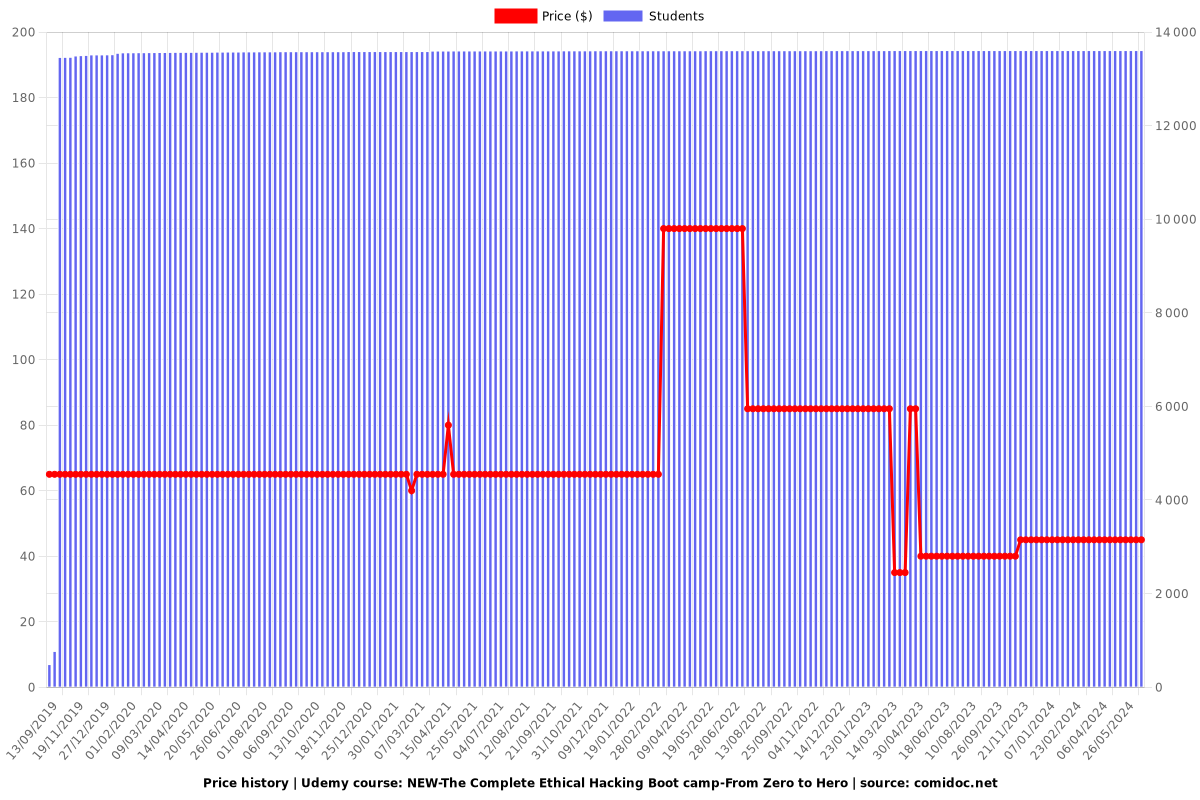
Price
Rating
Enrollment distribution
Coupons
| Submit by | Date | Coupon Code | Discount | Emitted/Used | Status |
|---|---|---|---|---|---|
| J.J | 11/10/2019 | 3DAYCOUPONS | 100% OFF | expired | |
| Lee Jia Cheng | 17/01/2020 | COURSEUN1TYWEB | 100% OFF | 10/7 | expired |