Title
Practical hacking and pentesting course for beginners
Learn practical hacking and pentesting with a step by step guide. A hands on approach to learn practical ethical hacking

What you will learn
Hacking and bypassing Windows login Passwords
Cracking Passwords for word, excel, Zip and Rar Files
How to Speed up password cracking with GPU based attacks
How to Install and use Password Cracking tools in Windows Environment
How to Extract Windows passwords from RAM with Mimikatz
Best cracking and hacking tools on both windows and Kali Linux
How to Hack Android Devices with Kali Linux
Hack & secure both WiFi & wired networks
Hacking Wireless Networks with modern tools
Web Hacking Basics
Practical Bug Bounty with DVWA
Hack Windows with Metasploit Framework
How to hack Windows and linux machines over the network
Create your own Hacking Lab in a Virtual Environment (Quick and Easy Way)
Install & use Kali Linux - a penetration testing operating system in an easy and efficient manner
How to scan targets efficiently to gather more information about the target
How to perform vulnerability assessment of a target
Analysing traffic with Wireshark
Why take this course?
Based on the detailed breakdown provided, it seems you're outlining a comprehensive curriculum for a hacking and penetration testing course aimed at beginners. The course covers a wide range of topics, including but not limited to:
-
Wi-Fi Network Hacking:
- Learning tools like Aircrack-ng and Hashcat.
- Understanding the process of cracking wifi passwords using different methods.
- Automating the process with single commands.
- Cracking Wi-Fi networks from Windows systems.
-
Office Files (Word, Excel, PowerPoint) Password Recovery:
- Protecting and then recovering passwords for office files.
- Using tools like John the Ripper and Hashcat.
- Installing these tools on both Linux and Windows.
- Removing various restrictions from office documents.
-
Practical Pentesting and Network Attacks:
- Introducing Metasploit and conducting attacks against targets.
- Scanning systems and performing vulnerability assessments.
- Extracting information, deploying keyloggers, and taking screenshots post-exploitation.
- Practicing pentesting with free tools.
-
Android Hacking and Pentesting:
- Setting up an Android VM for hacking purposes.
- Exploiting vulnerabilities in Android devices using payloads generated with msfvenom or adb (Android Debug Bridge).
-
Web Hacking and Bug Bounty for Beginners:
- Performing directory vulnerability analysis (Dirbusting).
- Working through challenges in the Damn Vulnerable Web Application (DVWA).
- Exploiting common web vulnerabilities such as SQL injection and XSS.
- Reconnaissance techniques specific to web applications.
- Understanding bug bounty fundamentals, including how to identify, report, and validate vulnerabilities.
- Learning defensive strategies to protect against attacks.
The course emphasizes hands-on, practical skills and is designed to be comprehensive and educational. It also includes ethical considerations, ensuring that students understand the importance of using their knowledge responsibly and within legal boundaries.
This curriculum is well-rounded and covers a variety of skill sets that are in high demand in the field of cybersecurity. It's important for anyone pursuing a career in this area to understand both offensive (pentesting) and defensive strategies, as well as the ethical implications of their actions.
Our review
Course Review Synthesis
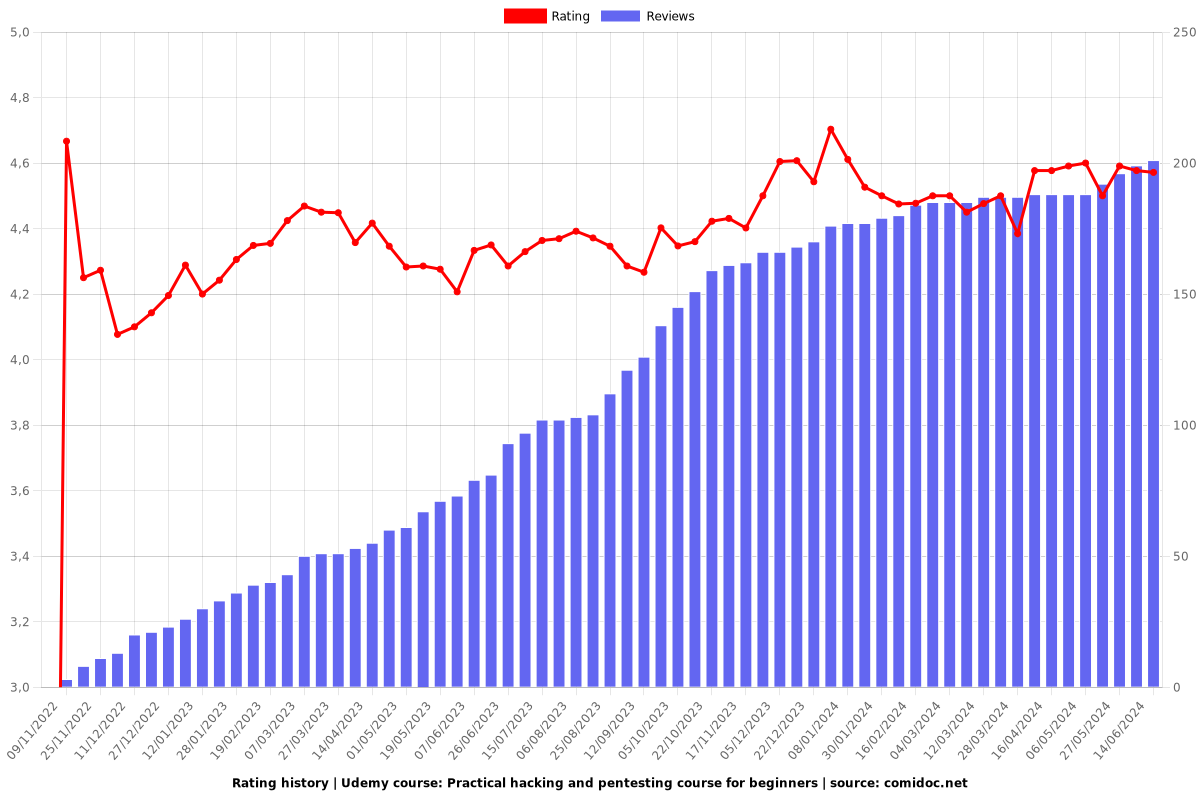
Overall Course Rating: 4.63/5
Pros of the Course:
-
Content Quality: The content is reported to be interesting and engaging with each step meticulously explained, which makes the learning process crystal clear.
-
Detailed Explanation: Each topic within the course seems to be covered thoroughly, providing students with a deep understanding of the subject matter.
-
Teaching Materials: Students have praised the teaching materials as top-notch, indicating that they are well-prepared and enhances the learning experience.
-
Lecture Formats: The lectures are accessible in multiple formats (likely video and PDF), offering flexibility for different learning preferences.
-
Course Structure: The course structure is designed to be simple and effective, which helps beginners grasp complex topics like hacking and cybersecurity much easier.
-
Educational Impact: Students have mentioned that the knowledge gained has already had a positive impact on their careers and they appreciate the efficient learning approach.
One student even goes as far as to say the course content is life-changing.
Cons of the Course (based on feedback):
-
Initial Immersion: One reviewer pointed out an initial difficulty in asking questions directly, which implies that there might be some room for improvement in the course's Q&A mechanism or support system early on.
-
Engagement Level: The feedback from one student indicates that a full assessment of the course may require completing all parts of the course, but the beginning was already interesting and the teaching style promising.
Additional Comments:
-
The mentor and spiritual team received special appreciation for their contributions to course materials, suggesting that the collaborative effort behind the scenes significantly impacts the quality of the course.
-
A student noted the availability of lectures in PDF format, which is a valuable feature for those who prefer or need printed materials, as well as for use offline.
Summary:
The course stands out with its comprehensive content, detailed explanations, and high-quality teaching materials. Students are appreciative of the simple yet effective teaching style and have already seen tangible benefits in their careers. While some improvements could be made to the initial course engagement or the Q&A process, overall, the course is highly recommended for anyone looking to learn about hacking and cybersecurity. It's a great resource that offers value both for practical application and for those looking to deepen their understanding of cyber security principles. Final Verdict: A Definite Must-Take Course for Aspiring Cyber Experts.
Charts
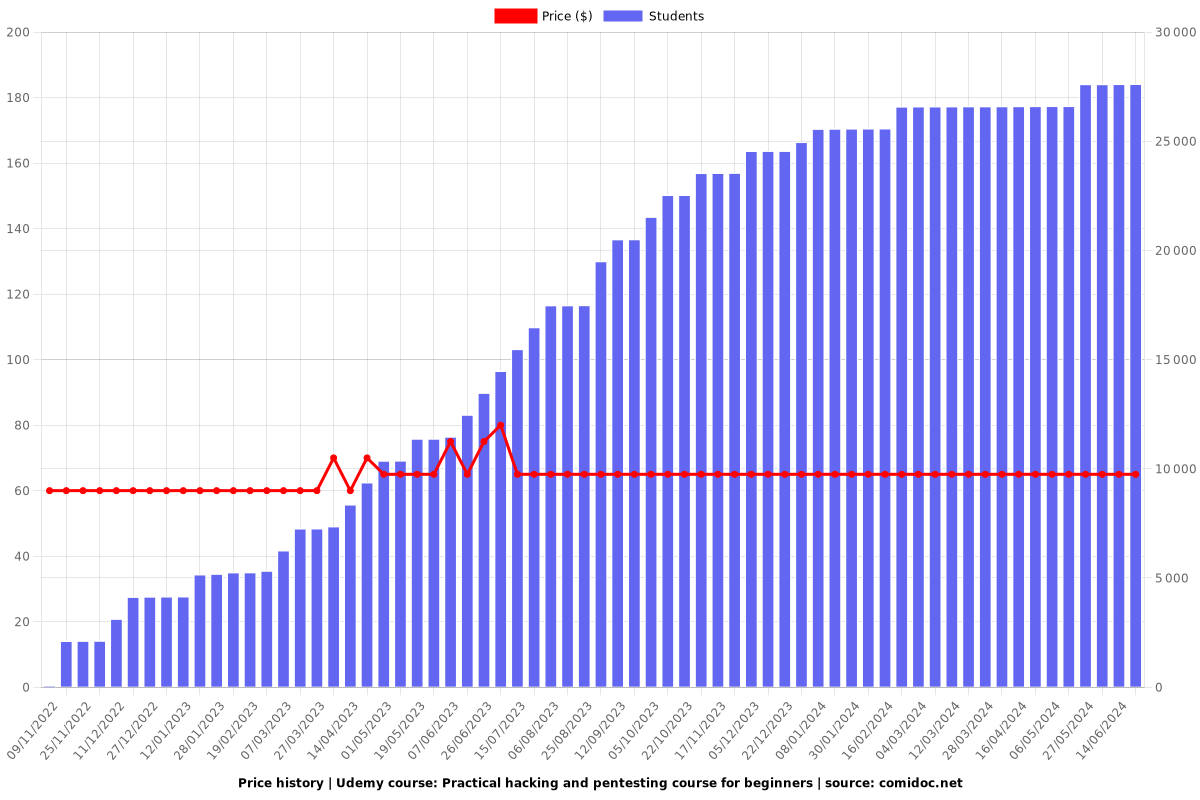
Price
Rating
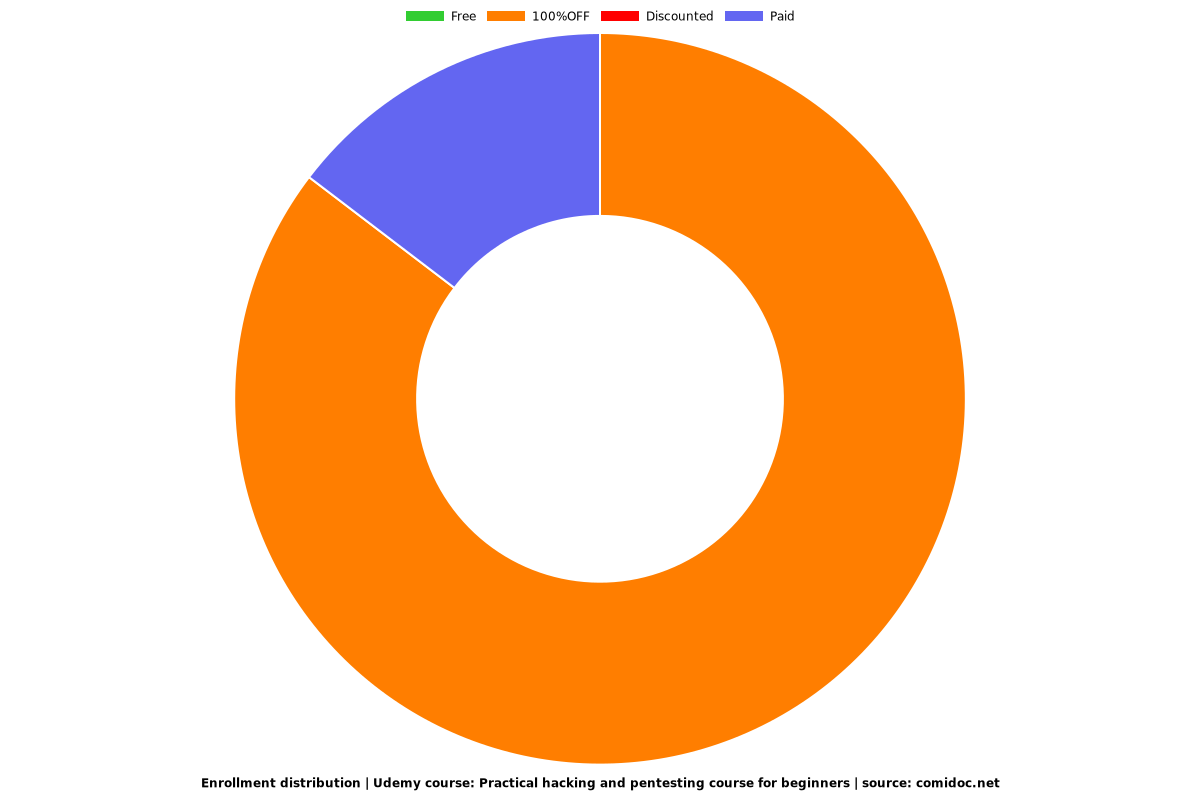
Enrollment distribution
Coupons
| Submit by | Date | Coupon Code | Discount | Emitted/Used | Status |
|---|---|---|---|---|---|
| - | 09/11/2022 | FREEDOM | 100% OFF | 1000/17 | expired |
| - | 11/11/2022 | HASSAN | 100% OFF | 100/64 | expired |
| - | 12/11/2022 | NOV1111 | 100% OFF | 1000/945 | expired |
| - | 08/12/2022 | BC86BA936F515B679817 | 100% OFF | 1000/898 | expired |
| - | 15/12/2022 | FREEFORDEC | 100% OFF | 1000/809 | expired |
| - | 14/01/2023 | 75A1B558ED0C3D7E9AA9 | 100% OFF | 1000/733 | expired |
| sultan hashim | 26/02/2023 | 1C9000B43FC5745BF6C7 | 100% OFF | 1000/952 | expired |
| - | 10/03/2023 | REVIEW-ME | 100% OFF | 1000/974 | expired |
| - | 30/03/2023 | A71CF4A30FF7A74506D4 | 100% OFF | 100/37 | expired |
| - | 11/04/2023 | 083F95EBAE7DCF9ECB95 | 100% OFF | 1000/884 | expired |
| - | 17/04/2023 | ENJOY-AND-REVIEW | 100% OFF | 1000/501 | expired |
| - | 21/04/2023 | 7C41485A44E53FBCAFE6 | 100% OFF | 1000/986 | expired |
| - | 13/05/2023 | DAVID123 | 100% OFF | 1000/774 | expired |
| - | 29/05/2023 | 6FE320148FEB3F419681 | 100% OFF | 100/47 | expired |
| - | 07/06/2023 | 43B0A739989ED2E9F12A | 100% OFF | 1000/434 | expired |
| - | 17/06/2023 | B0494E3C3720E27481A0 | 100% OFF | 1000/981 | expired |
| - | 27/06/2023 | 445E3D14ED044F38D432 | 100% OFF | 1000/814 | expired |
| - | 09/07/2023 | 9C3EB8E49383D54B635F | 100% OFF | 1000/788 | expired |
| - | 15/07/2023 | E4B1868B2D7689847619 | 100% OFF | 1000/988 | expired |
| - | 29/07/2023 | FEE467A7103752A757D7 | 100% OFF | 1000/268 | expired |
| - | 25/08/2023 | 94160C01BD73C54BD6A0 | 100% OFF | 1000/913 | expired |
| - | 28/08/2023 | 901FB01FB14B45EE3B3F | 100% OFF | 1000/995 | expired |
| - | 09/09/2023 | FF42C0588B98FF8957C5 | 100% OFF | 1000/958 | expired |
| - | 24/09/2023 | 10A59A6E2DAD9D4D81A3 | 100% OFF | 1000/707 | expired |
| - | 07/10/2023 | 215DC521B52065C8A36D | 100% OFF | 1000/941 | expired |
| - | 22/10/2023 | D7F40F422AA2DB96CBA7 | 100% OFF | 1000/721 | expired |
| - | 25/11/2023 | CBAAC07E2892FA89D0DD | 100% OFF | 1000/999 | expired |
| - | 30/12/2023 | A80BF82721D0E79E318E | 100% OFF | 1000/988 | expired |
| - | 18/02/2024 | B4CCE4312312384E2ACD | 100% OFF | 1000/780 | expired |
| - | 28/03/2024 | ABA5BA935D7F53596285 | 85% OFF | expired | |
| Muhammad | 18/05/2024 | 487E34B5AD21E3D1975C | 100% OFF | 1000/885 | expired |
| - | 27/06/2024 | 06B9A91F68B06D43D17B | 100% OFF | 1000/919 | expired |
| - | 07/08/2024 | B7A46B56004EC2C41F53 | 100% OFF | 1000/898 | expired |
| - | 18/11/2024 | CD384C54ABE56069D5FF | 100% OFF | 1000/965 | expired |
| - | 22/01/2025 | CA5A50619BADC763D7A3 | 100% OFF | 1000/939 | expired |
| - | 04/02/2025 | 9A291B2DCE0F3D2C1394 | 100% OFF | 1000/878 | expired |
| - | 18/02/2025 | 129E0DAB475A011C3C3E | 100% OFF | 1000/980 | expired |
| - | 22/02/2025 | E4A2F9F043FDA7C80485 | 100% OFF | 1000/931 | expired |
| - | 06/03/2025 | B3DD090F972D7CED2C7A | 100% OFF | 1000/382 | working |