Practical Hacking: Undetectable Malware
Become a Practical Ethical Hacker : Learn How to bypass antiviruses and firewall also learn how to defense against it.
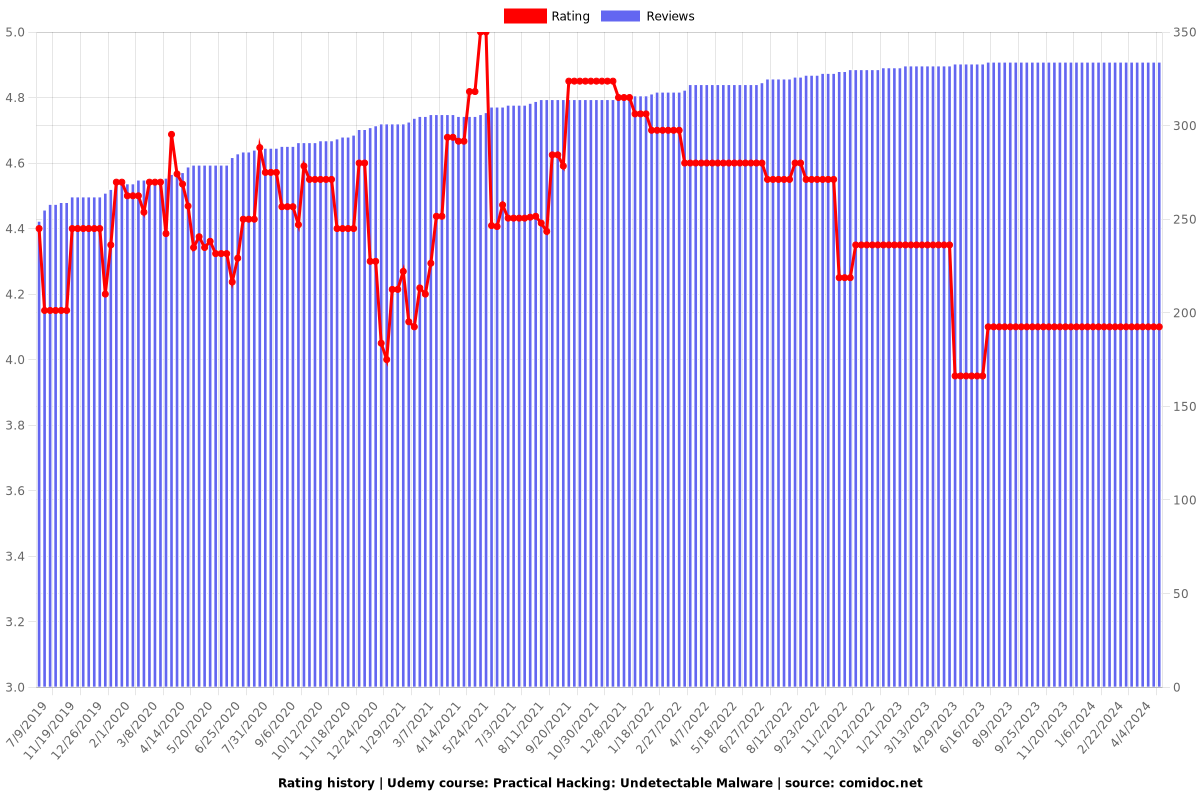
4.10 (334 reviews)

2,701
students
1.5 hours
content
Apr 2024
last update
$39.99
regular price
What you will learn
You will be able to bypass any up-to-date antivirus
You will learn advance payload creation
You will Learn How to bind your payload with image file
You will Learn How to change extension of your payload to jpg
You will learn how to maintain access once you have gain it
Why take this course?
🎉 **Master the Art of Ethical Hacking with Arsalan Saleem!** 🎓
**Course Title:** Practical Hacking: Undetectable Malware
🚀 **Course Headline:** Become a Practical Ethical Hacker: Learn to Bypass Antiviruses and Firewalls – Also, Defend Against Them!
---
**Introduction:**
Dive into the world of cybersecurity with our comprehensive course designed for aspiring ethical hackers. In this course, you will learn from the ground up how to create undetectable malware that can bypass state-of-the-art defenses. Learn to think like an attacker and understand the vulnerabilities within systems that are up-to-date and fully patched. This is not just about breaking in; it's about understanding the intricacies of cyber defense to better protect your own systems.
---
**Course Breakdown:**
🔍 **Understanding the Enemy's Terrain:**
- **Bypassing Antivirus and Firewall Protections:** Discover how malware evades detection using advanced techniques.
- **Social Engineering and Initial Access:** Learn how to craft targeted attacks to gain entry into systems.
🛠️ **Crafting Undetectable Malware:**
- **Malware Development Basics:** Get hands-on experience in creating your own malicious software.
- **Binding Payloads with Everyday Files:** Master the art of hiding malicious code within files that typically pass security inspections.
🌍 **Remote Hacking Techniques:**
- **Cross-Border System Compromise:** Explore methods to access and exploit systems from anywhere in the world.
- **Evading Detection Across Networks:** Understand how to maintain an undetected presence within a network.
🕳️ **Maintaining Access:**
- **"Maintaining Access":** Learn the strategies used to keep unauthorized access open over extended periods, even after detection.
🛡️ **Defending Against Malware:**
- **Understanding Attack Vectors:** Gain insights into how malware operates and how to protect against it.
- **Implementing Security Countermeasures:** Learn the best practices for securing systems against sophisticated cyber attacks.
---
**Why Take This Course?**
🚀 **Practical Skills:** Gain hands-on experience with real-world scenarios that will challenge and expand your knowledge of ethical hacking.
🛡️ **Real-World Relevance:** The skills you learn in this course are directly applicable to protecting systems from malicious attacks.
👥 **Community Support:** Join a community of like-minded learners and professionals who are passionate about cybersecurity.
📅 **Flexible Learning:** Study at your own pace, with materials accessible 24/7, so you can learn when it fits into your schedule.
---
**Your Instructor:**
👤 **Arsalan Saleem:** An experienced cybersecurity expert and ethical hacker, Arsalan brings a wealth of knowledge to the course, providing you with insider tips and tricks that are both practical and effective.
---
Enroll now to embark on your journey towards becoming a proficient ethical hacker. With "Practical Hacking: Undetectable Malware," you'll not only learn how to breach systems but also, crucially, how to defend against such threats. Secure your future in cybersecurity today! 🔒🔥
Screenshots

Our review
---
**Overview:**
The course in question offers a deep dive into the creation of undetectable malware, focusing on payload binding and the use of Veil 3.0 framework to evade antivirus detection. It is praised for its clarity, up-to-date content, and practical approach to ethical hacking, with a particular emphasis on the advanced level topics covered.
**Pros:**
* **Comprehensive Content:** The course is highly informative and covers advanced topics in a way that is easy to understand, despite being at an advanced level.
* **Practical Techniques:** Real-world applications are emphasized, with instructors demonstrating how to overcome weaknesses in Metasploit using Veil 3.0.
* **Up-to-Date Material:** The content is described as up to date and applicable to current hacking scenarios.
* **Clear Instructions:** The instructions provided are clear, and the course material includes detailed PDFs for future reference.
* **Research-Based:** The instructor's research contributes significantly to the quality of the course material.
* **Real-World Focus:** The course focuses on the attacking phase, which is considered very important in real-world hacking scenarios.
* **Easy to Follow Tutorials:** For those who are familiar with the basics of ethical hacking, the tutorials are up to date and very easy to follow.
* **Advanced Topic Coverage:** The course covers specific topics, such as payload creation and Gaining Access and maintaining access, in complete detail with practical examples.
**Cons:**
* **Technology Updates:** Some users have noted that the course may not include the most current tools or frameworks used today.
* **Audio Quality Issues:** A few reviews mention difficulties with hearing the instructor due to poor microphone quality.
* **Course Completeneness:** There are indications that the course might feel rushed, as if it wasn't fully completed or developed as some other courses on the platform.
* **Expectation of Technical Development:** Some learners were hoping for a more technical development of exploits rather than reliance on frameworks like Metasploit and Veil.
---
**Final Verdict:**
This course is highly recommended for those interested in ethical hacking, particularly for individuals who wish to delve into the practical aspects of creating undetectable malware using Veil 3.0. The course stands out due to its detailed explanations, real-world applications, and up-to-date content. However, potential learners should be aware that some parts of the course may feel outdated if they are looking for the most cutting-edge techniques. It is also recommended to ensure that the instructor's audio quality is improved in future iterations of the course for a better learning experience. Despite these minor drawbacks, the course is overall an excellent resource for anyone looking to enhance their hacking skills in a practical and comprehensive manner.
Charts
Price
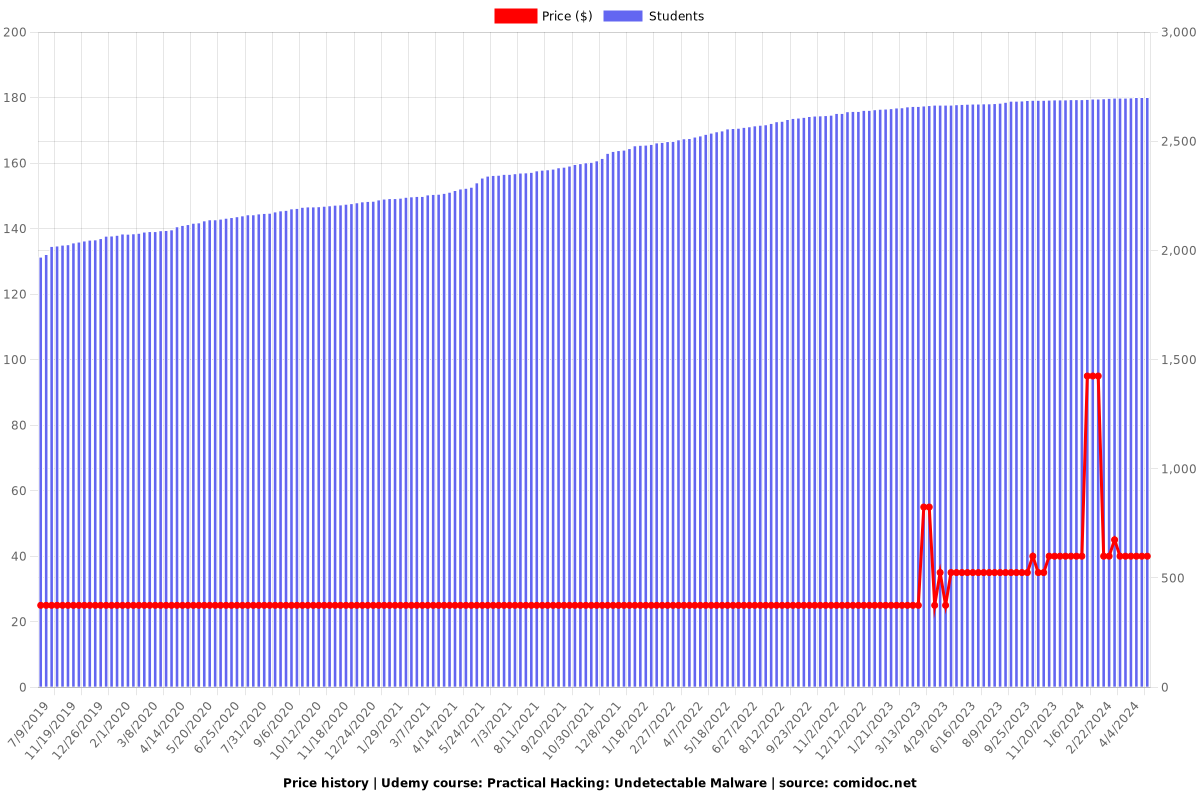
Rating
Enrollment distribution
Related Topics
1541392
udemy ID
2/5/2018
course created date
7/9/2019
course indexed date
Bot
course submited by