Hacking and Securing JSON Web Tokens (JWT)
Learn how to exploit insecure JWT implementations using practical exercises

What you will learn
Students will get Indepth knowledge about Json Web Tokens (JWT)
Students will learn JWT Implementation Weaknesses
Students will learn various practical JWT Attacks
Students will learn how to securing JWT Implementations
Students will learn how to do JWT based REST API Security testing
Students will learn how HS256 and RS256 Algorithms work
Students will learn how Hash Based Message Authentication Code (HMAC) works
Students will learn how RSA Digital Signatures work
Students will learn how to use openssl command line client to practice Cryptographic algorithms
Why take this course?
This course teaches various insecure implementations of Json Web Token (JWT) based REST APIs. This course begins by introducing students to the fundamental Json Web Token concepts. Even though, this is an entry level to intermediate level course, we encourage you to take this course if you already have basic Web Security knowledge as this course is designed to provide knowledge specific to Json Web Tokens and it does not cover the fundamentals of Web Security Testing and REST API Security Testing. Do note that the course involves a lot of JWT fundamental concepts and only the last module covers the practical attacks against JWT. So, please get your expectation right before jumping on the course. Rest Assured, you will feel confident about Json Web Tokens and JWT Security testing after completing this course.
As a bonus, a Virtual Machine is provided with all the source code used in the labs. So, you can change the code to have few more vulnerable implementations of JWT.
Screenshots
Reviews
Charts
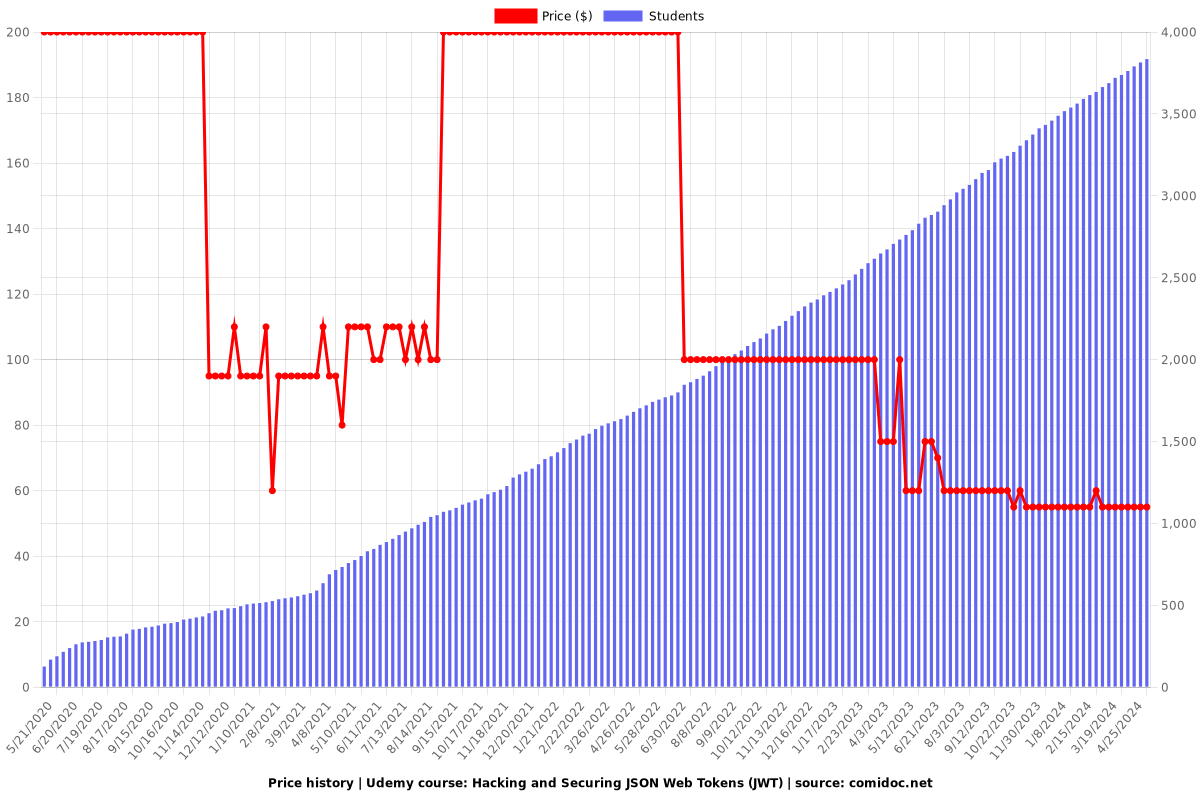
Price
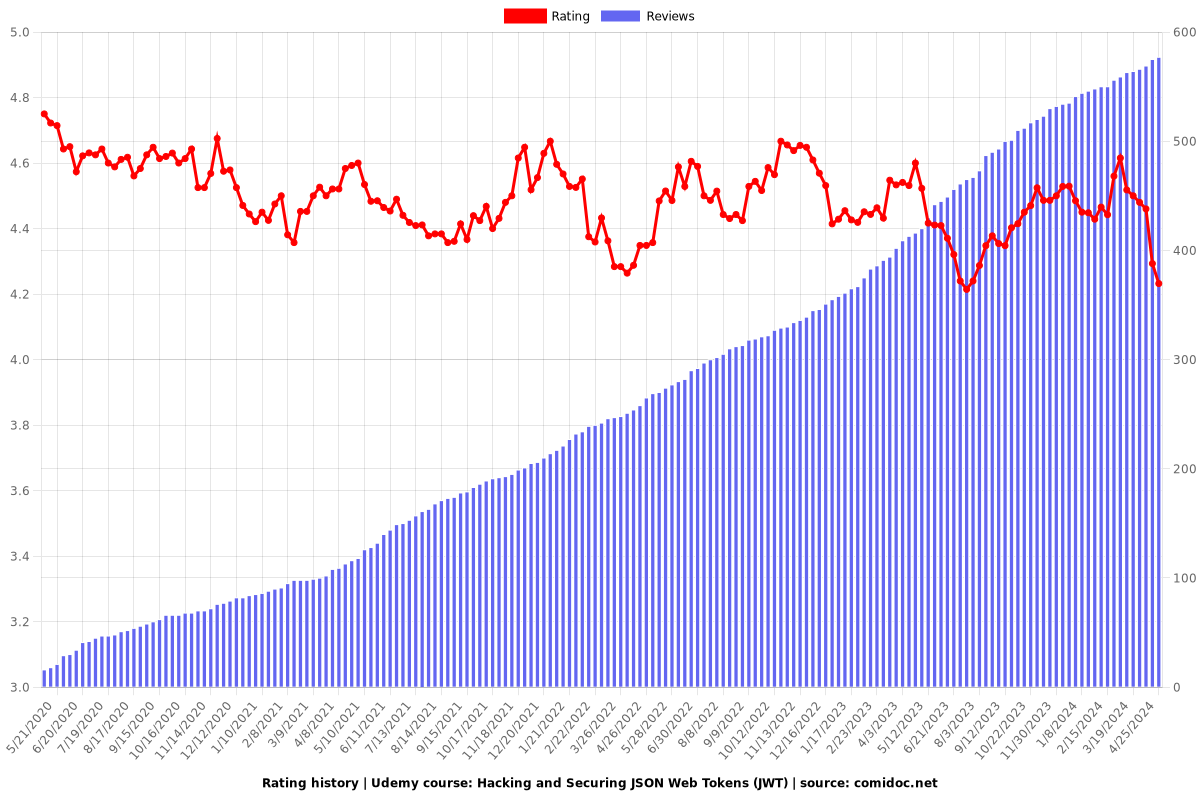
Rating
Enrollment distribution