Don's Introduction to Ethical Hacking for Beginners
My answer to the question "How do I learn how to hack?"
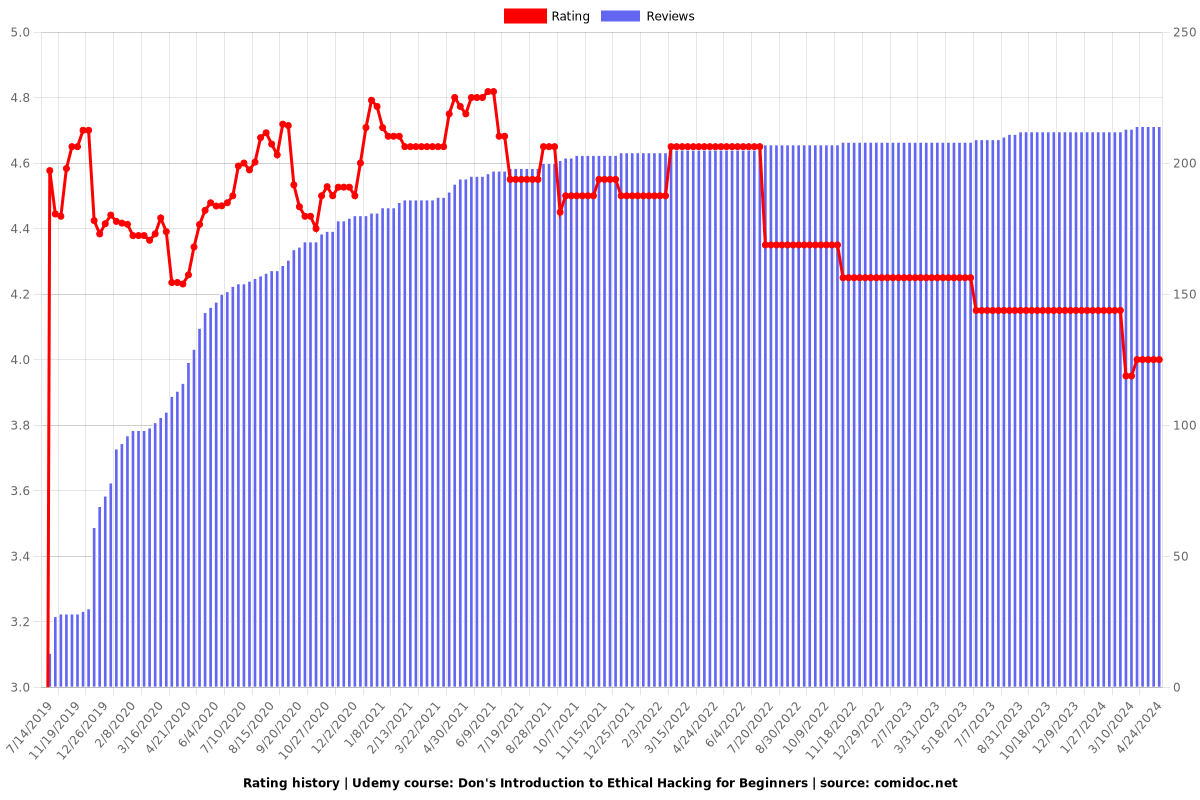
4.00 (214 reviews)

13,831
students
12 hours
content
May 2022
last update
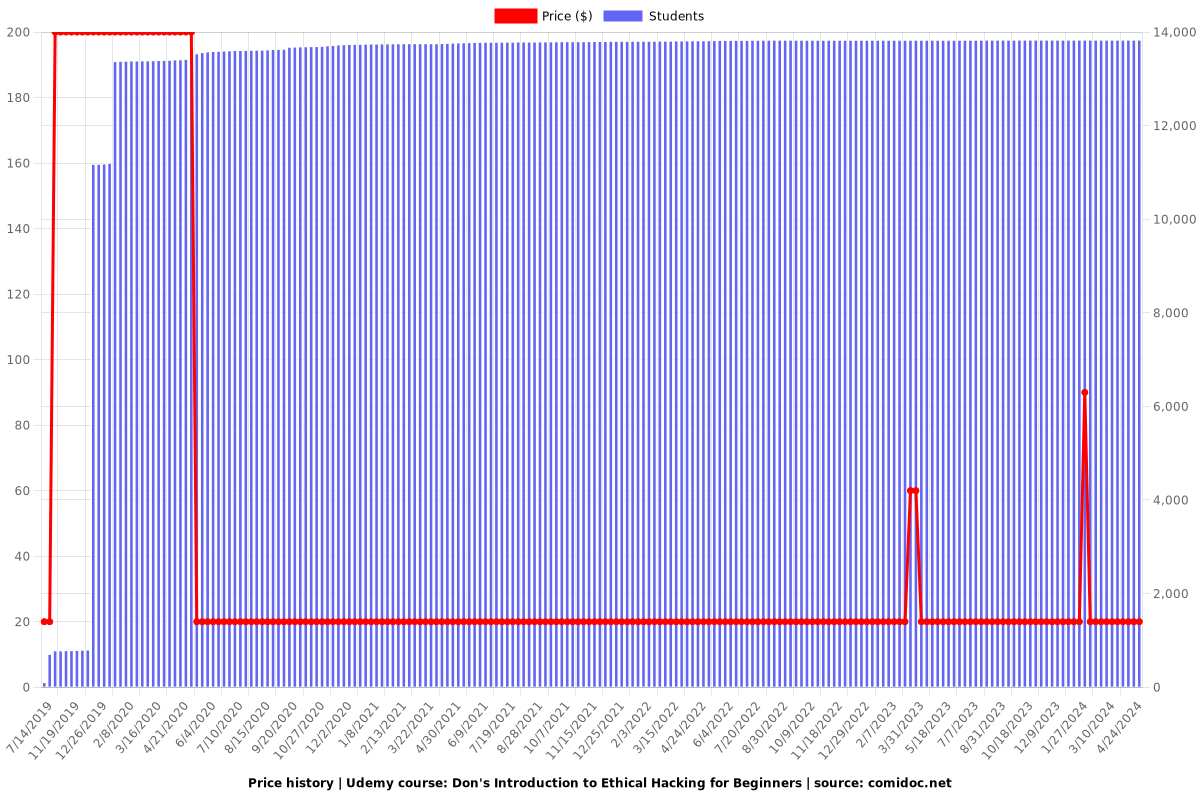
$19.99
regular price
What you will learn
Ethical Hacking
Penetration Testing
Virtual machines
Hacker hats
BASH
BASH Scripting
Netcat
Nmap
Passive Reconnaissance
Email enumeration
WHOIS Fingerprinting
DNS Enumeration
Active Reconnaissance
Dirb
Dirbuster
Google hacking
Metadata
Public password databreaches
Security Vulnerabilities - Heartbleed
Security Vulnerabilities - Shellshock
Security Vulnerabilities - Dirty COW
Nikto
Arachni
Wordpress Scanning
Nessus
Metasploit
Meterpreter
MSF Venom
EternalBlue Exploitation
Web / HTTP / HTML
SQL Injection
Cross-Site Scripting
HTML Injection
Burpsuite
Session Hijacking
Session Fixation
Local File Include
Remote File Include
OS Command Injection
Cross-Site Request Forgery
Direct Object Reference
Buffer Overflow
Denial of Service attacks
Linux Password Cracking
Windows Password Cracking
Linux Privilege Escalation
Windows Privilege Escalation
BurpSuite
Why take this course?
---
GroupLayout: **Don's Introduction to Ethical Hacking for Beginners**
---
### **Course Headline:**
🔍 **My Answer to the Question "How Do I Learn How to Hack?"**
---
### **Course Description:**
**Hello! 🚀**
Don here, and I'm not just any cybersecurity enthusiast—I'm a seasoned penetration tester and ethical hacker with years of experience in the field. I've encountered countless individuals asking the same question: "Where do I even start?" Well, you've come to the right place!
**Why This Course? 🤔**
This hands-on, practical course is crafted specifically to address the curiosity and ambition of those who want to understand the world of ethical hacking. **Don's Introduction to Ethical Hacking for Beginners** will take you on an exhilarating journey through the dark corridors of cybersecurity, exploring topics such as:
- 💻 **Exploitation Techniques**
- ⚔️ **Website Hacking**
- 🛠️ **SQL Injection (SQLi)**
- 🔄 **Cross-Site Scripting (XSS)**
- 🧬 **Buffer Overflow Vulnerabilities**
- 🤖 **Using Metasploit**
- 🔑 **Privilege Escalation**
...and much more!
### **Course Highlights:**
- **Zero Pre-Requisites**: No prior knowledge? No problem! I've designed this course for absolute beginners. We'll start from the basics and build up your skills.
- **Learn by Doing**: I'll guide you through every concept with real-world examples. You'll see me perform exploitations, and then you'll get to try it out yourself against secured Virtual Machines I've set up for safe learning.
- **Practical Experience**: With access to tailor-made VMs, you'll have the opportunity to put your newfound skills into practice. This isn't just theory; it's hands-on learning that will solidify your understanding of ethical hacking.
### **What You'll Learn:**
✅ Gain an introduction to the world of ethical hacking.
✅ Understand common vulnerabilities and how they can be exploited.
✅ Learn the basics of penetration testing and how to approach it.
✅ Explore various tools like Metasploit that are essential for a hacker's toolkit.
✅ Discover the techniques attackers use to compromise systems and learn how to defend against them.
✅ Build a solid foundation to continue your journey into cybersecurity.
### **Course Structure:**
1. **Introduction to Cybersecurity**: We'll start with the basics, laying down the groundwork for what ethical hacking is and why it's crucial.
2. **Basic Tools and Technologies**: You'll be introduced to the essential tools you'll need, including how to navigate through them.
3. **Exploitation Basics**: Learn about different types of vulnerabilities and how they can be exploited.
4. **Hands-On Practice**: With a set of VMs ready for you to experiment with, you'll apply what you've learned in real-time.
5. **Advanced Exploitation Techniques**: Delve deeper into complex hacks and understand the mechanisms behind them.
6. **Real-World Scenarios**: We'll cover case studies where ethical hacking made a difference, giving you insights into how to approach complex problems.
### **Join Me on This Adventure! 🌟**
If you've ever been curious about the world of cybersecurity or if you're serious about making a career out of ethical hacking, this course is your gateway. Sign up today and embark on an unforgettable learning journey with Don as your guide. Let's decode the language of hackers together!
---
**Enroll Now and Transform Your Cybersecurity Perspective! 🛡️💻**
Screenshots




Our review
🌟 **Course Review for Ethical Hacking 101** 🌟
### Overall Rating: 4.00
#### Pros:
- **Engaging and Easy to Understand Content**: The course is praised for its clear and engaging delivery. Don's teaching style is described as effective, with a focus on practical application that makes it easy to grasp the concepts being taught.
- **Well-Structured Material**: The material provided in the course is reported to be comprehensive and well-structured, offering a solid foundation for those new to the field of Ethical Hacking.
- **Interesting and Informative**: Many students found the course very interesting and felt they learned a great deal from it, appreciating the practical demonstrations that accompany theoretical explanations.
- **Positive Student Experience**: The overall student experience is positive, with many completing the course and finding it engaging. One student even commented on the course being the only one from several they completed on Udemy.
- **General Knowledge of Basics**: For beginners, the course provides a good general knowledge of the basics of hacking, which is useful for understanding the fundamentals.
#### Cons:
- **Audio Quality Concerns**: A few reviews mentioned that the audio quality in certain videos was not optimal, which could potentially make those sections harder to understand.
- **Desire for More In-Depth Content and Practical Exercises**: Some students would like more in-depth coverage of topics and practical tasks to apply what they've learned directly. This feedback suggests there is an opportunity to expand the course content to provide more hands-on experience.
- **Virtual Machine Setup**: One student pointed out that instructions for obtaining the virtual machines used in the course were not provided, which could be a barrier to completing certain practical tasks.
- **File Size Concerns**: One reviewer had a question about downloading a 20GB work file, expressing uncertainty about whether to do so.
#### Additional Feedback:
- **Completion and Engagement**: The course is noted for its ability to hold students' engagement, as evidenced by the fact that many completed the course despite often having multiple courses from Udemy in progress.
- **Room for Improvement**: While the course is appreciated, there is a clear demand for additional content and tasks that allow for more practical application of the skills taught.
In summary, this Ethical Hacking course on Udemy is well-received for its engaging delivery, comprehensive material, and usefulness in providing a foundation in ethical hacking. However, there is room for improvement in terms of audio clarity, content depth, and providing clear instructions for necessary software setup. Overall, it's a solid offering that can be made even stronger with some enhancements based on student feedback.
Charts
Price
Rating
Enrollment distribution
2445008
udemy ID
7/5/2019
course created date
7/14/2019
course indexed date
Bot
course submited by