Ethical Hacking Primer: From OWASP Top 10 to DVWA
Going over the OWASP Top 10 theory and a hands-on lab for DVWA

What you will learn
An overview of the OWASP Top 10 Web Vulnerabilities List
Fundamental prevention methods against OWASP Top 10 vulnerabilities
Basic compnonents of the BurpSuite proxy
Bruteforce attacks
Command injection attacks
SQL injection attacks
XSS (Cross-Site Scripting) attacks
Why take this course?
We will explore web application vulnerabilities, go over the OWASP Top 10 web vulnerabilities list and do some hands-on exercises on Damn vulnerable web application with the virtual machine provided.
This course is not a complete ethical hacking course, it is a primer. The goal of this course is to familiarize beginners to the OWASP Top 10 vulnerabilities, go over remediation methods and provide a lab environment where they can practice the newly acquired skills. High severity vulnerabilities such as SQL injection, Bruteforce attacks, Command Injection, XSS and CSRF will be exploited and the methodology to detect and exploit these vulnerabilities will be explained.
This course would be ideal for anyone who is considering starting a training course on cyber security. If you have just signed up to platforms such as TryHackMe or HacktheBox, this course will also give a fundamental idea about vulnerabilities you may learn to exploit.
This course can also provide web developers with some ideas on building more secure software as we will discuss some aspects of the secure software development lifecycle.
I have provided you with a free virtual machine image you will be able to download, and build your own lab environment locally. So you can follow along with this course and keep practicing afterwards.
Screenshots



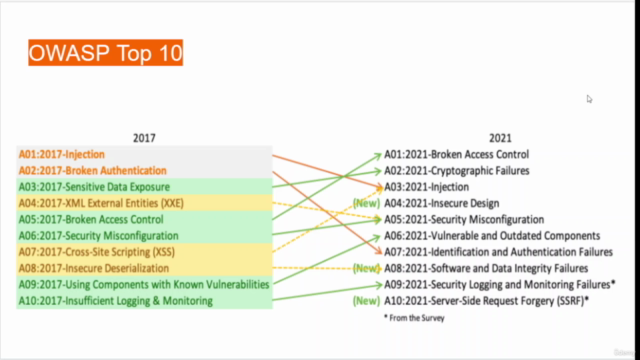
Charts
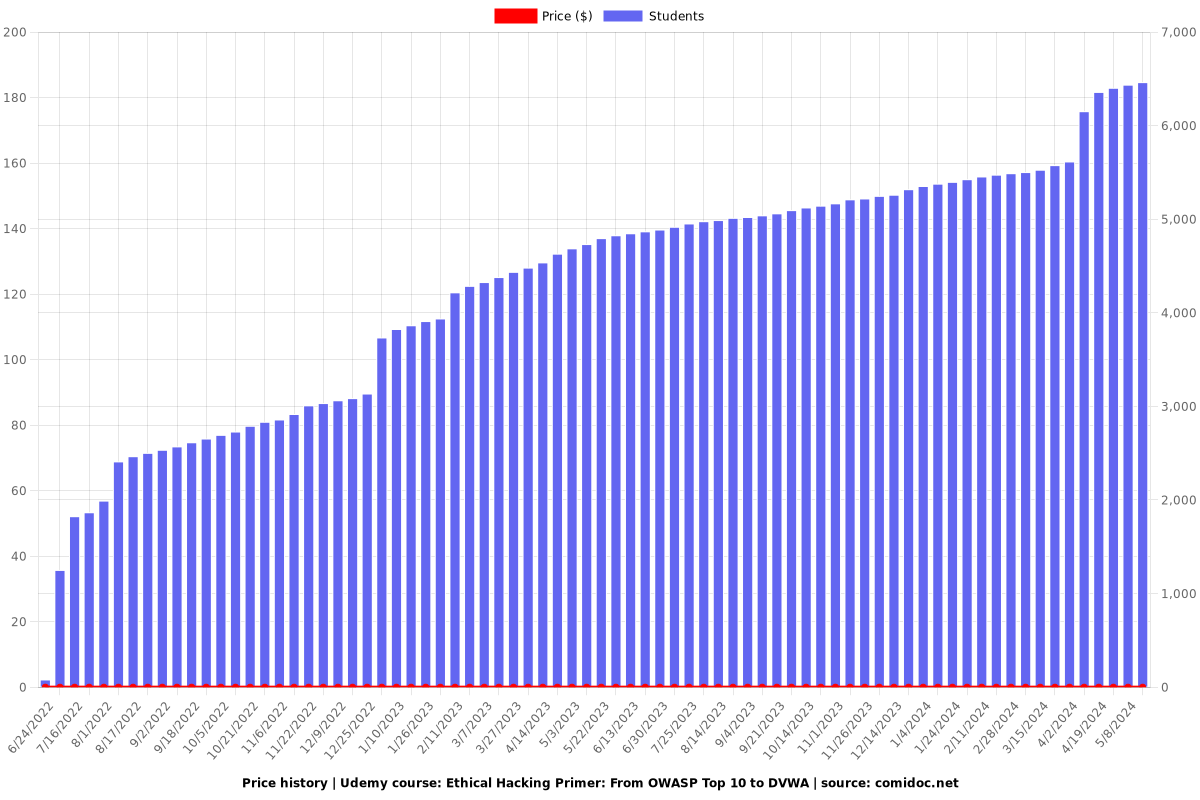
Price
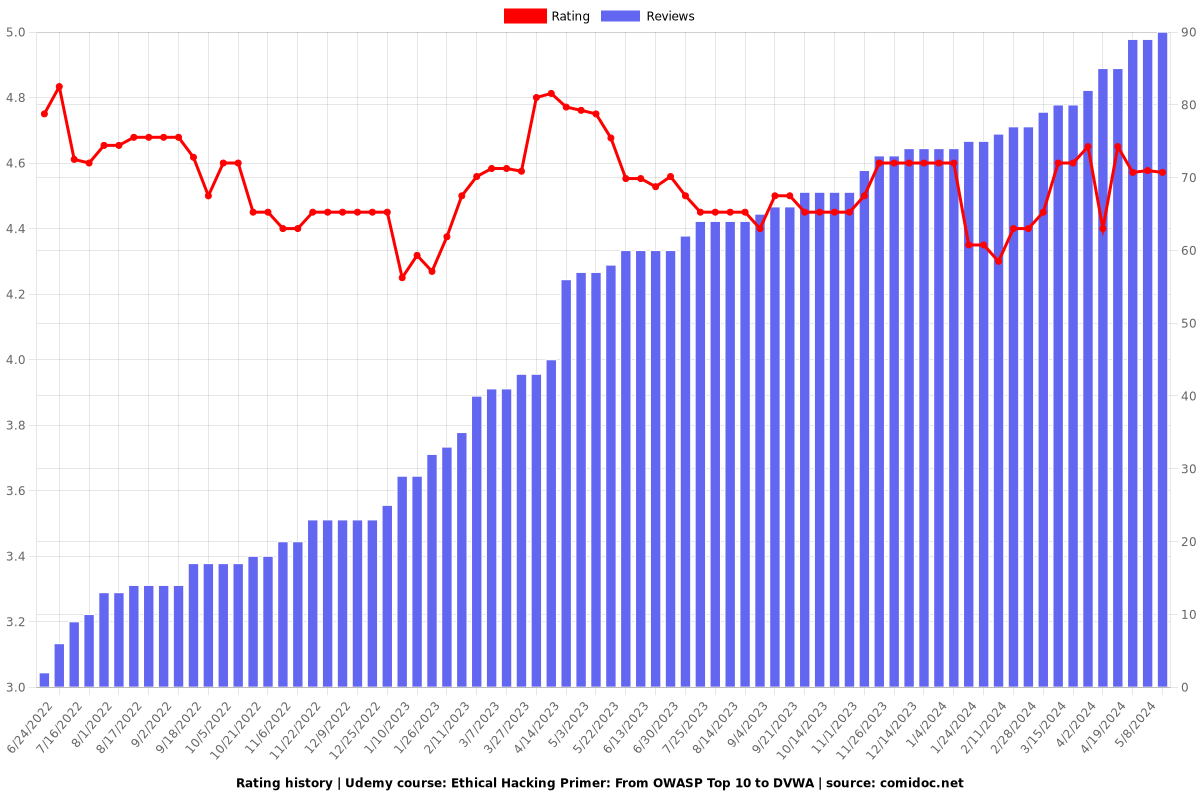
Rating
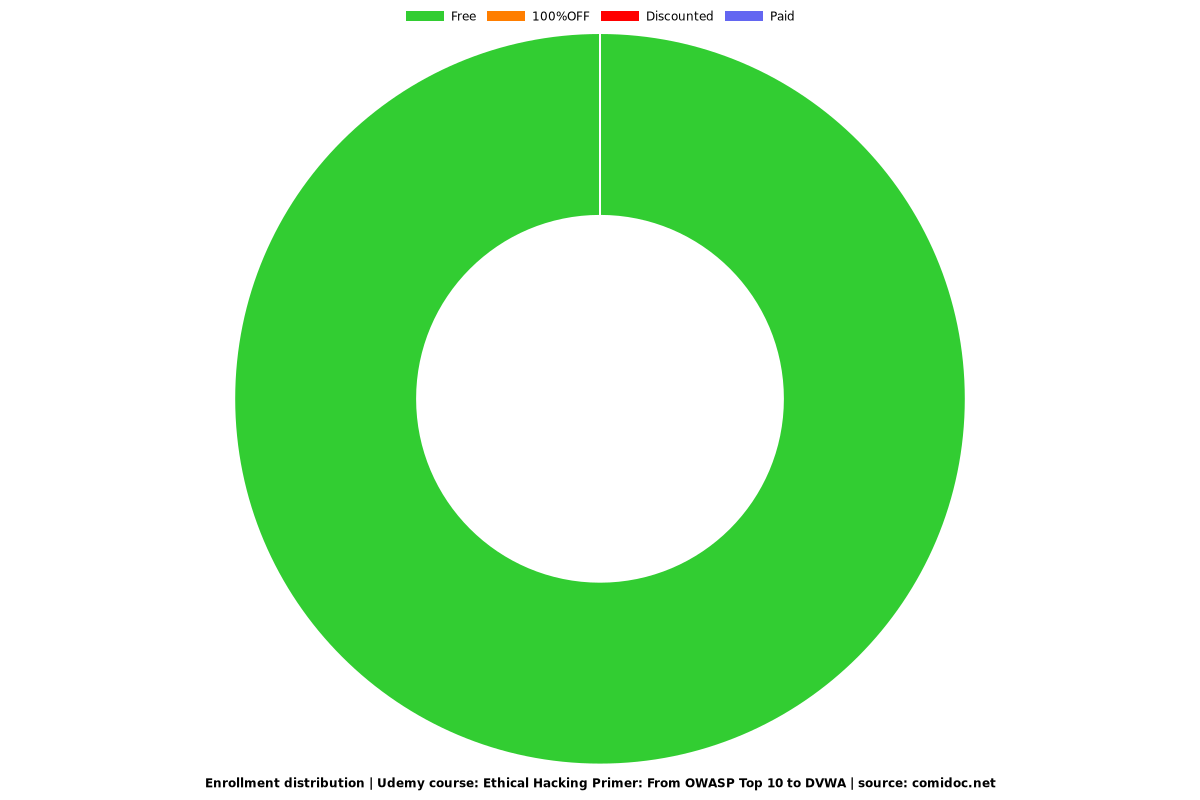
Enrollment distribution