Windows Privilege Escalation Penetration Testing - Part III
Enumeration and Exploitation of Windows Vulnerabilities and Misconfigurations to Access an Administrator Shell.

What you will learn
Way to get our service and products (Tools & Gift related to the course: FREE software & hardware) at our Facebook .com/JRDcademy page to excel in this course.
Multiple methods for escalating privileges on a Windows system; Enumeration and Exploitation
How to level up your ethical hacking, penetration testing and cybersecurity skills to boost your career
Most used tools which can help identify potential privilege escalation vulnerabilities on a Windows system.
Why take this course?
This course teaches the concept of "Windows Privilege Escalation with a Lab-intro for Linux", from a basic perspective such as how permissions work, to in-depth coverage and demonstrations of actual privilege escalation techniques.
This course is aimed for beginners, intermediate to advanced users who are hungry to know how to discover and exploit novel escalation paths on patched fully patched Windows machines. Everything in this course is carefully explained [step-by-step].
Course has been designed in a way so that any novice, (from Zero level) to the advanced level of people in cyber security field can easily understand and can be well-benefited.
In this course, we supply to you not only videos for the practice, but also we provide a Lab along with some other files which are exclusively self-explanatory (a step-by-step process) so that we make it easier to learn according to the obligations that you might face while you want to continue with your practice.
This is a 100% hands-on course as you will be using the same strategies and techniques in an offensive security team and advanced adversaries use to escalate privileges on Windows endpoints after they have gained initial access and established a foothold.
We use MetaSploit framework as well as Manual Exploitation to perform the privilege escalation. Everything is carefully explained and deconstructed so you can understand why and how it works.
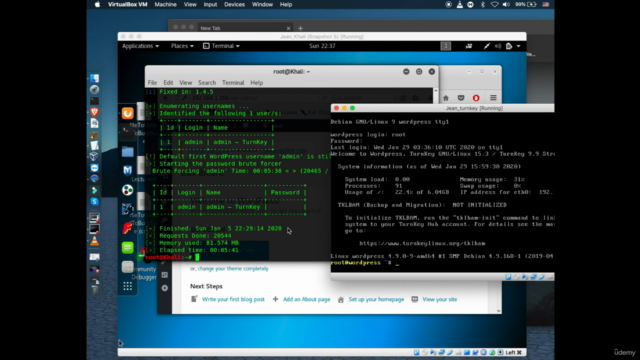
Screenshots
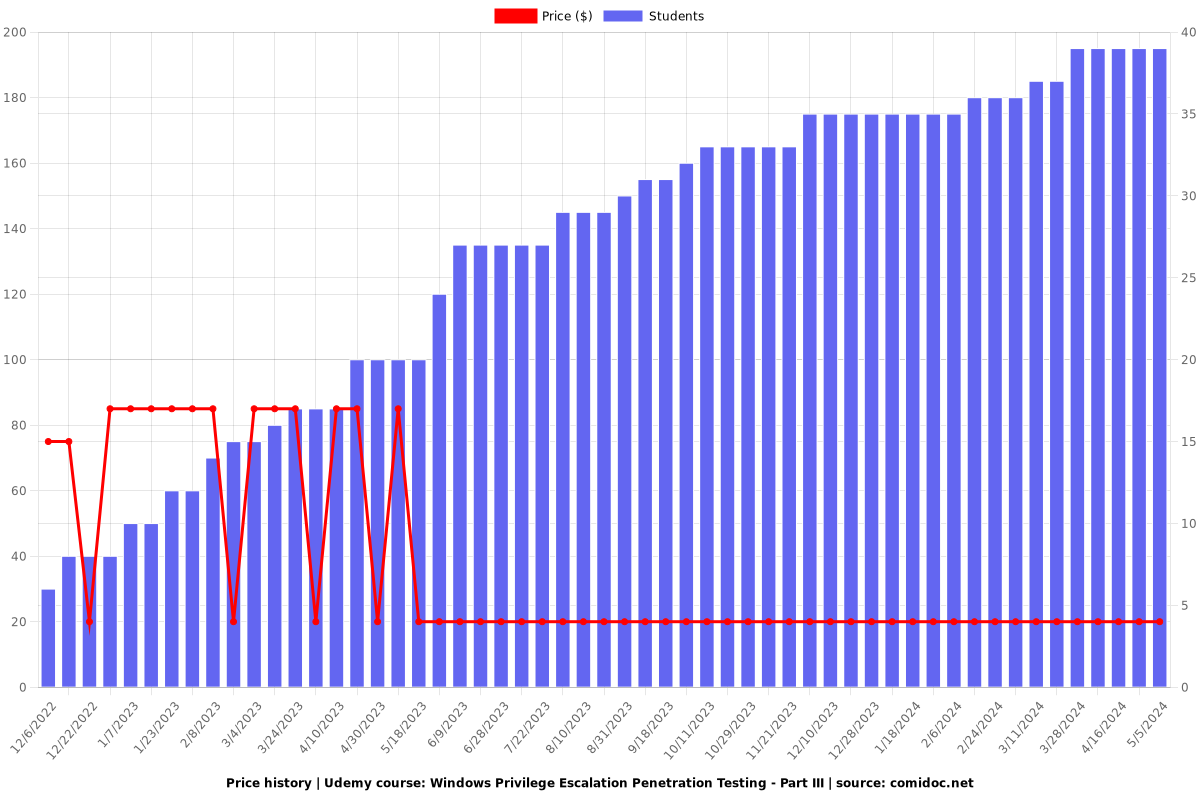
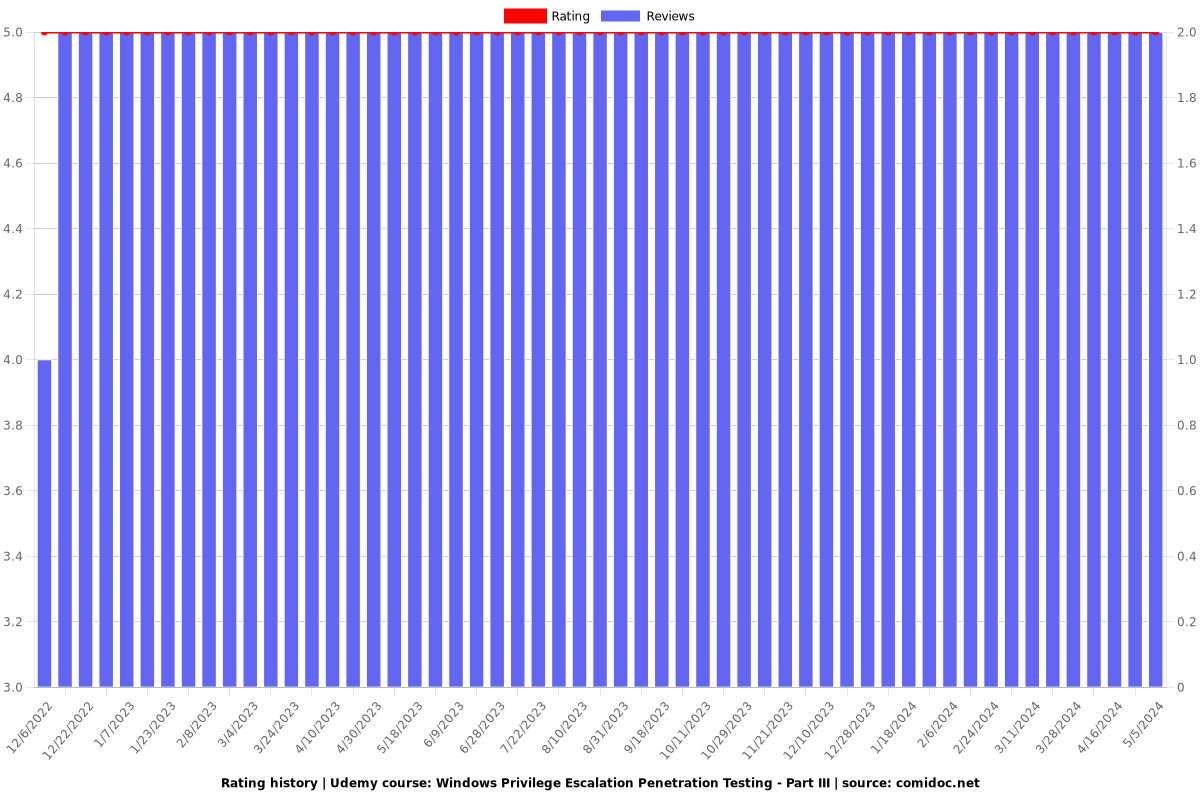
Charts
Price
Rating
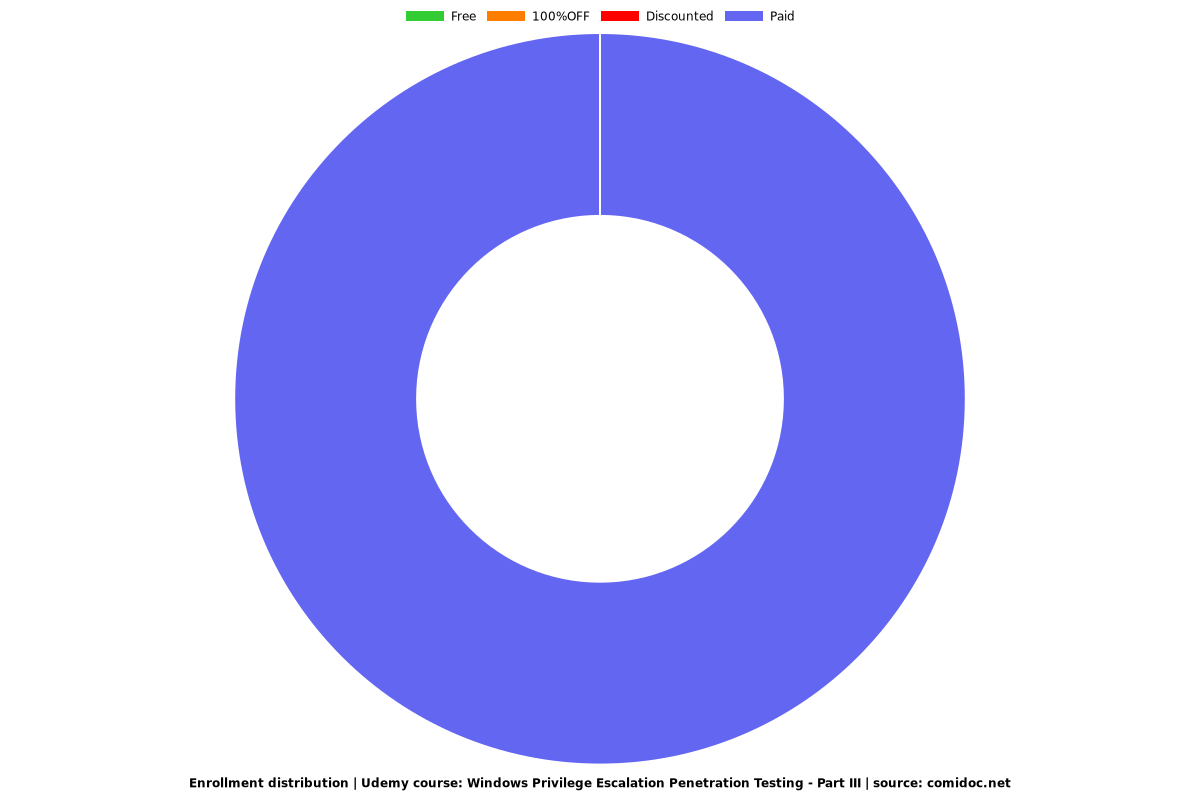
Enrollment distribution