Linux Heap Exploitation - Part 1
Learn hands-on GLIBC heap exploitation with HeapLAB.

What you will learn
Scripting exploits with pwntools
Introspecting the heap with pwndbg
The House of Force technique
The Fastbin Dup technique
The Unsafe Unlink technique
The Safe Unlink technique
The House of Orange technique
Using one-gadgets to drop a shell
Leveraging a single-byte heap overflow to drop a shell
Why take this course?
For nearly 20 years, exploiting memory allocators has been something of an art form. Become part of that legacy with HeapLAB.
The GNU C Library (GLIBC) is a fundamental part of most Linux desktop and many embedded distributions; its memory allocator is used in everything from starting threads to dealing with I/O. Learn how to leverage this vast attack surface via different heap exploitation techniques, from the original "Unsafe Unlink" to the beautiful overflow-to-shell "House of Orange".
In this hands-on course, students will alternate between learning new techniques and developing their own exploits based on what they've learned. We'll make use of the pwntools and pwndbg frameworks to drop shells from vulnerable practice binaries, and you'll take on challenges that test what you've learned.
Content
Introduction
The House of Force
The Fastbin Dup
CHALLENGE: Fastbin Dup 2
Unsafe Unlink
Safe Unlink
The House of Orange
CHALLENGE: One-Byte
Farewell
Screenshots
Reviews
Charts
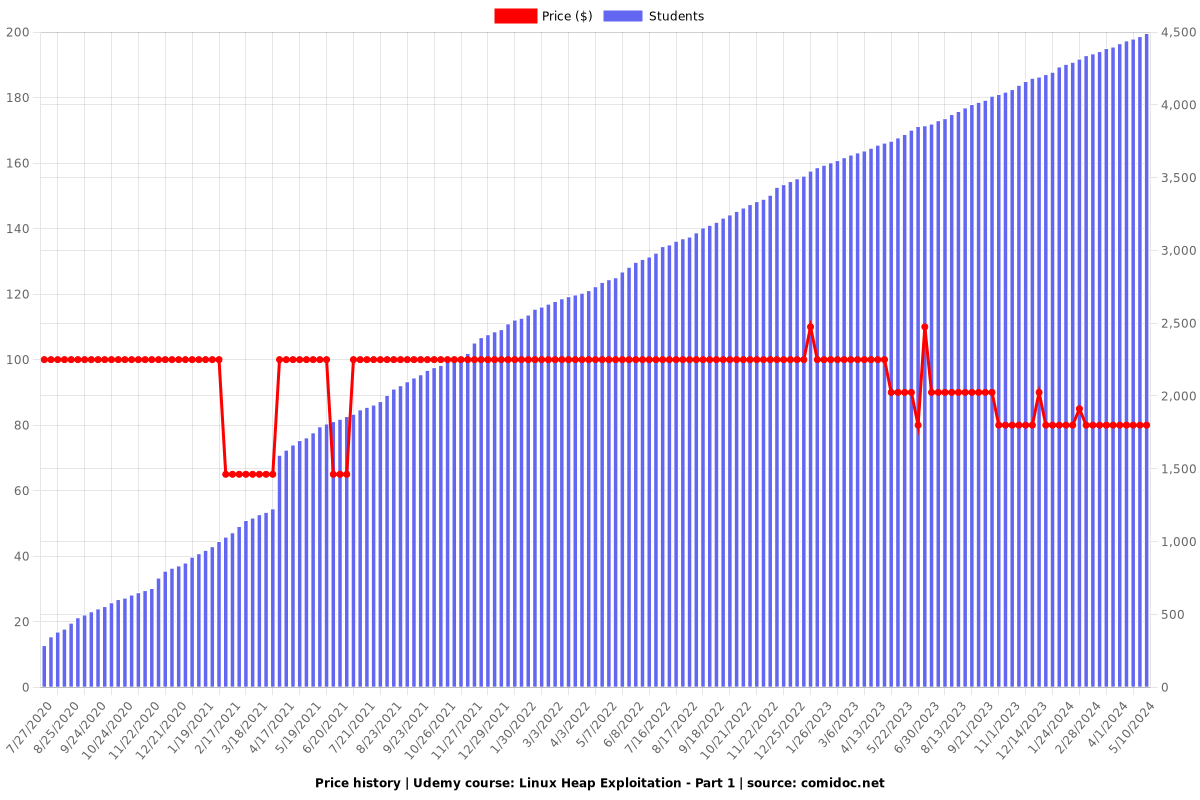
Price
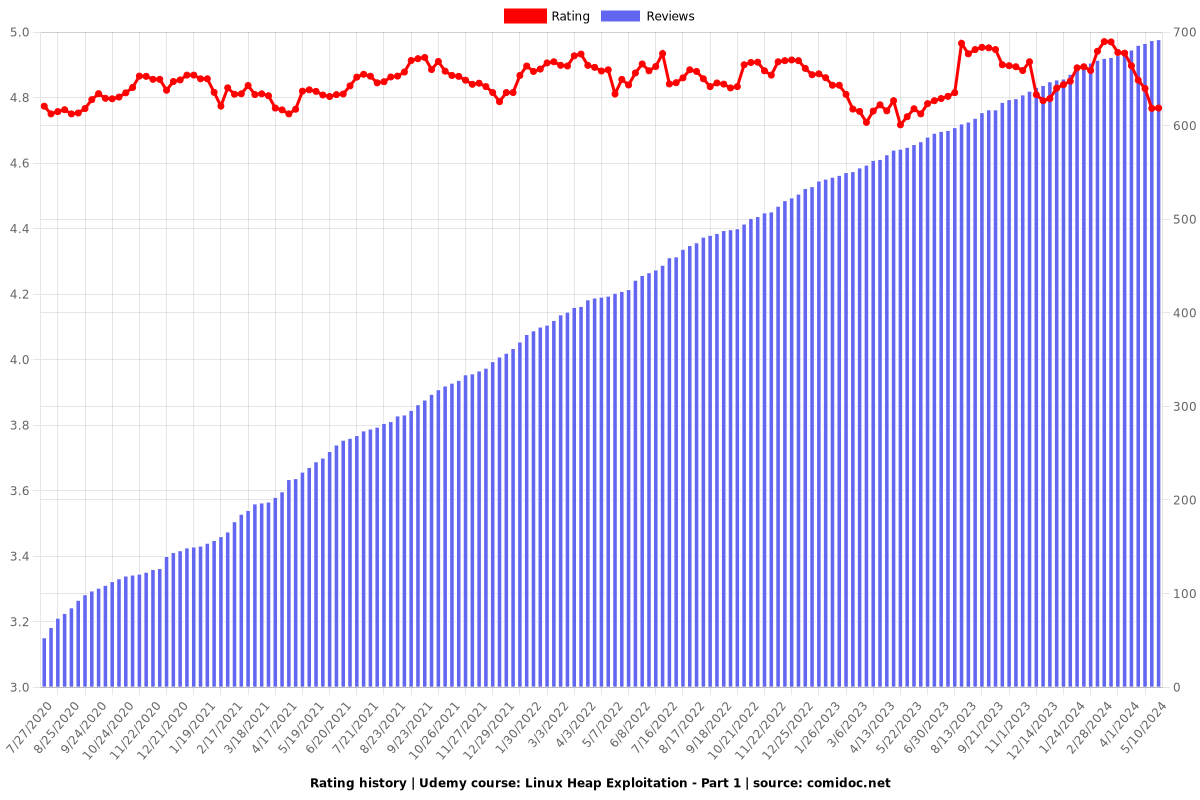
Rating
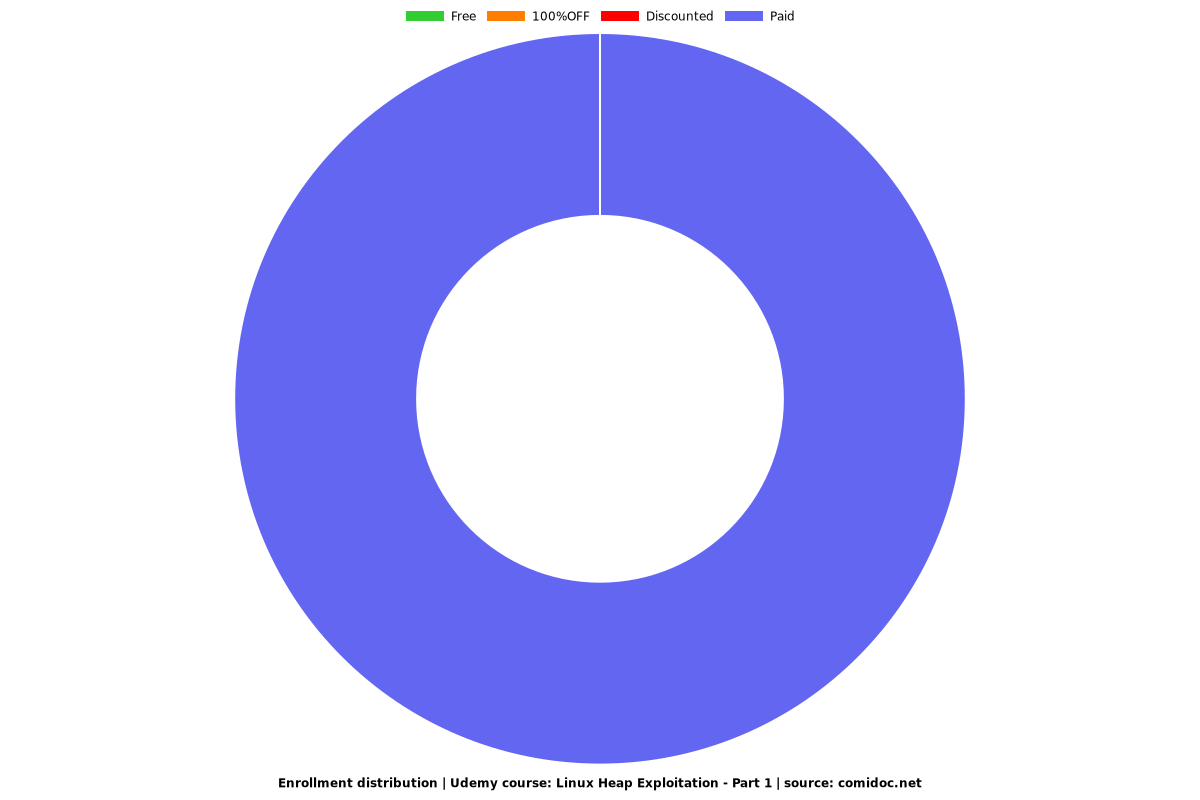
Enrollment distribution