Learning Python Web Penetration Testing
Make your applications attack-proof by penetration testing with Python

What you will learn
Understand the web application penetration testing methodology and toolkit
Interact with web applications using Python and the Requests library
Write a web crawler/spider with the Scrapy library
Create an HTTP bruteforcer based on Requests
Create a Password bruteforcer for Basic, NTLM, and Forms authentication
Detect and exploit SQL injections vulnerabilities by creating a script all by yourself
Intercept and manipulate HTTP communication using Mitmproxy
Why take this course?
With the huge growth in the number of web applications in the recent times, there has also been an upsurge in the need to make these applications secure. Web penetration testing is the use of tools and code to attack a website or web app in order to assess its vulnerabilities to external threats. While there are an increasing number of sophisticated ready-made tools to scan systems for vulnerabilities, the use of Python allows testers to write system-specific scripts, or alter and extend existing testing tools to find, exploit, and record as many security weaknesses as possible.
This course will walk you through the web application penetration testing methodology, showing you how to write your own tools with Python for every main activity in the process. It will show you how to test for security vulnerabilities in web applications just like security professionals and hackers do.
The course starts off by providing an overview of the web application penetration testing process and the tools used by professionals to perform these tests. Then we provide an introduction to HTTP and how to interact with web applications using Python and the Requests library. Then will follow the web application penetration testing methodology and cover each section with a supporting Python example. To finish off, we test these tools against a vulnerable web application created specifically for this course.
Stop just running automated tools—write your own and modify existing ones to cover your needs! This course will give you a flying start as a security professional by giving you the necessary skills to write custom tools for different scenarios and modify existing Python tools to suit your application’s needs.
About The Author
Christian Martorella has been working in the field of Information Security for the last 16 years, and is currently working as Principal Program Manager in the Skype Product Security team at Microsoft. Christian's current focus is on software security and security automation in a Devops world.
Before this, he was the Practice Lead of Threat and Vulnerability for Verizon Business, where he led a team of consultants in delivering security testing services in EMEA for a wide range of industries including Financial Services, Telecommunications, Utilities, and Government.
Christian has been exposed to a wide array of technologies and industries, which has given him the opportunity to work in every possible area of IT security and from both sides of the fence, providing him with a unique set of skills and vision on Cyber Security.
He is the co-founder and an active member of Edge-Security team, who releases security tools and research. Christian has contributed to open source security testing and information gathering tools such as OWASP WebSlayer, Wfuzz, theHarvester, and Metagoofil, all included in Kali, the penetration testing Linux distribution.
Christian presented at Blackhat Arsenal USA, Hack.Lu, What The Hack!, NoConName, FIST Conferences, OWASP Summits, OWASP meetings (Spain, London, Portugal, and Venice), and Open Source Intelligence Conference (OSIRA). In the past, Christian has organized more than 20 FIST Conferences in Barcelona, providing a forum for professionals and amateurs interested in Security Testing. Christian holds a Master's degree in Business Administration from Warwick Business School, and multiple security certifications such as CISSP, CISM, CISA, OPSA, and OPST.
Content
Introduction
Interacting with Web Applications
Web Crawling with Scrapy
Resources Discovery
Password Testing
Detecting and Exploiting SQL Injection Vulnerabilities
Intercepting HTTP Requests
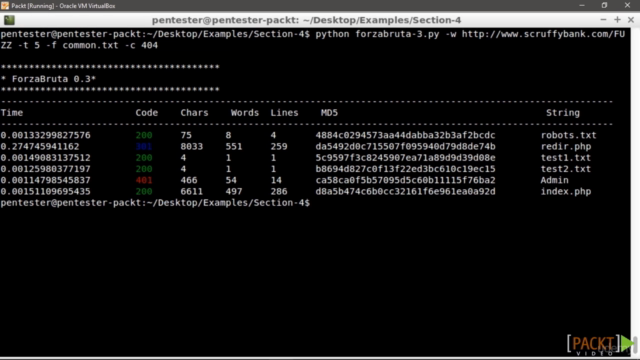
Screenshots

Reviews
Charts
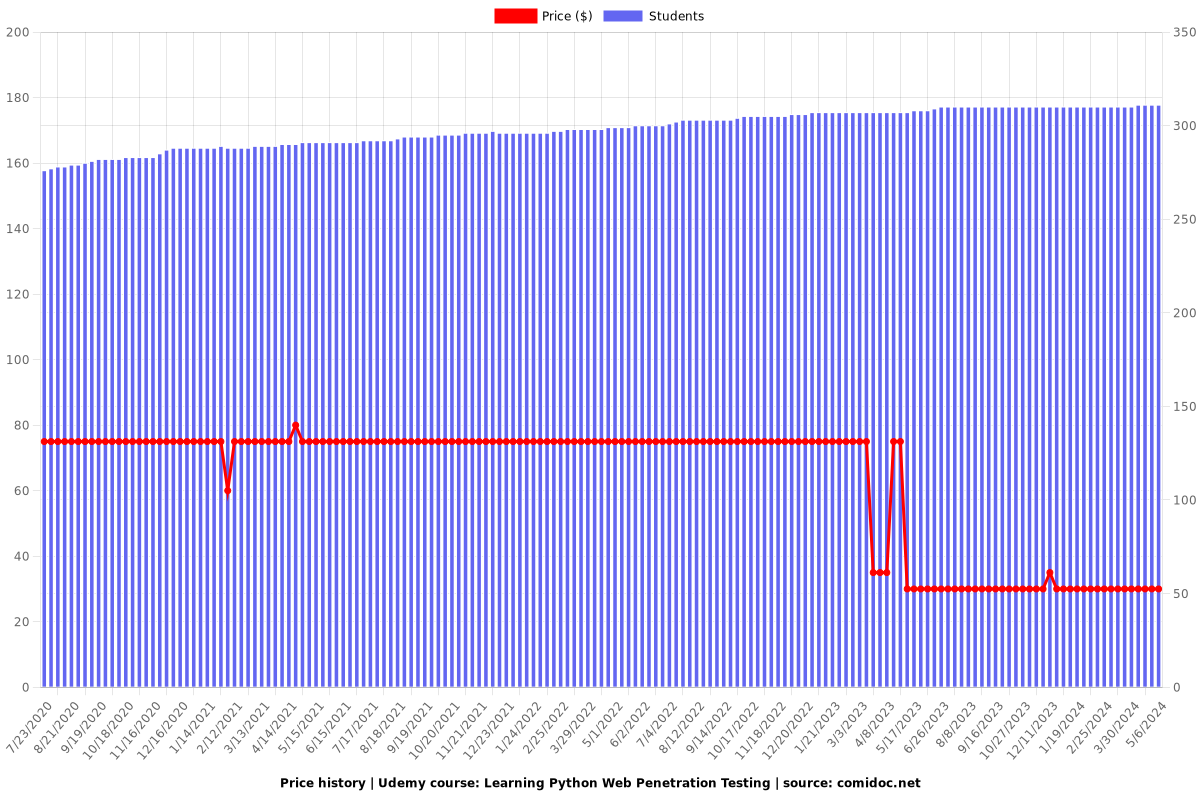
Price
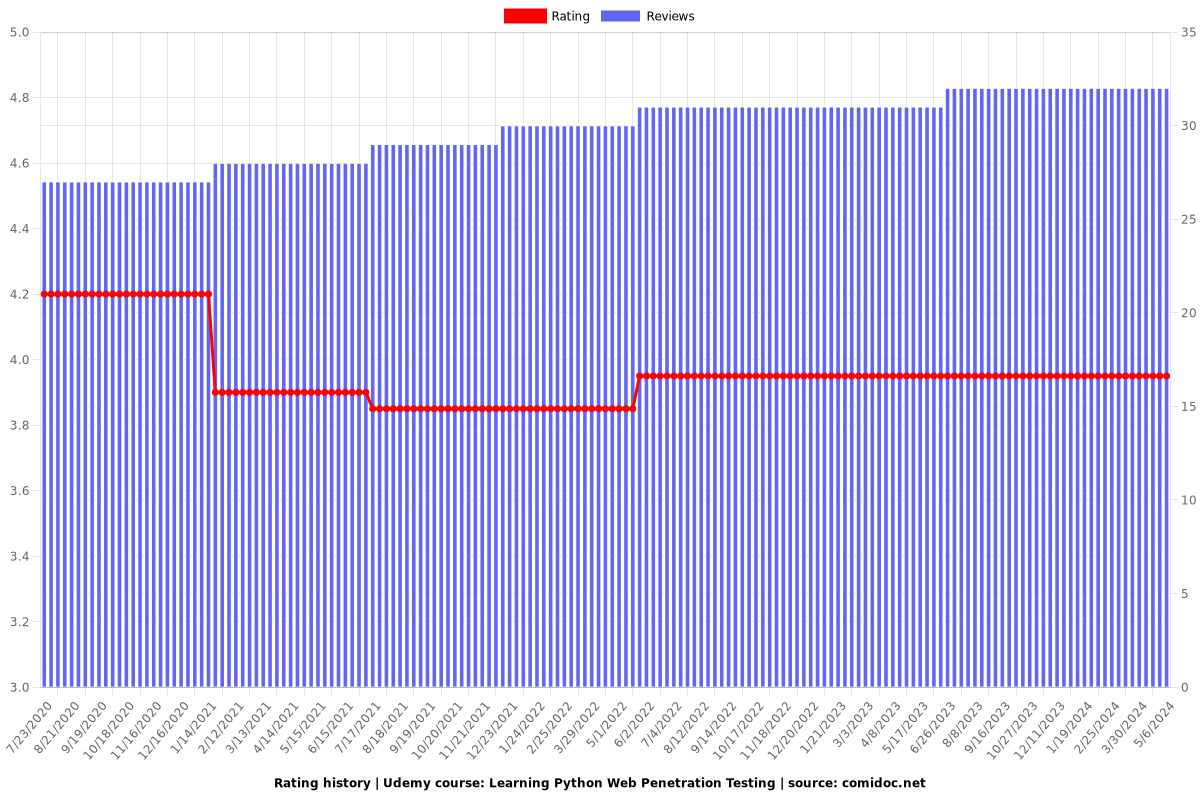
Rating
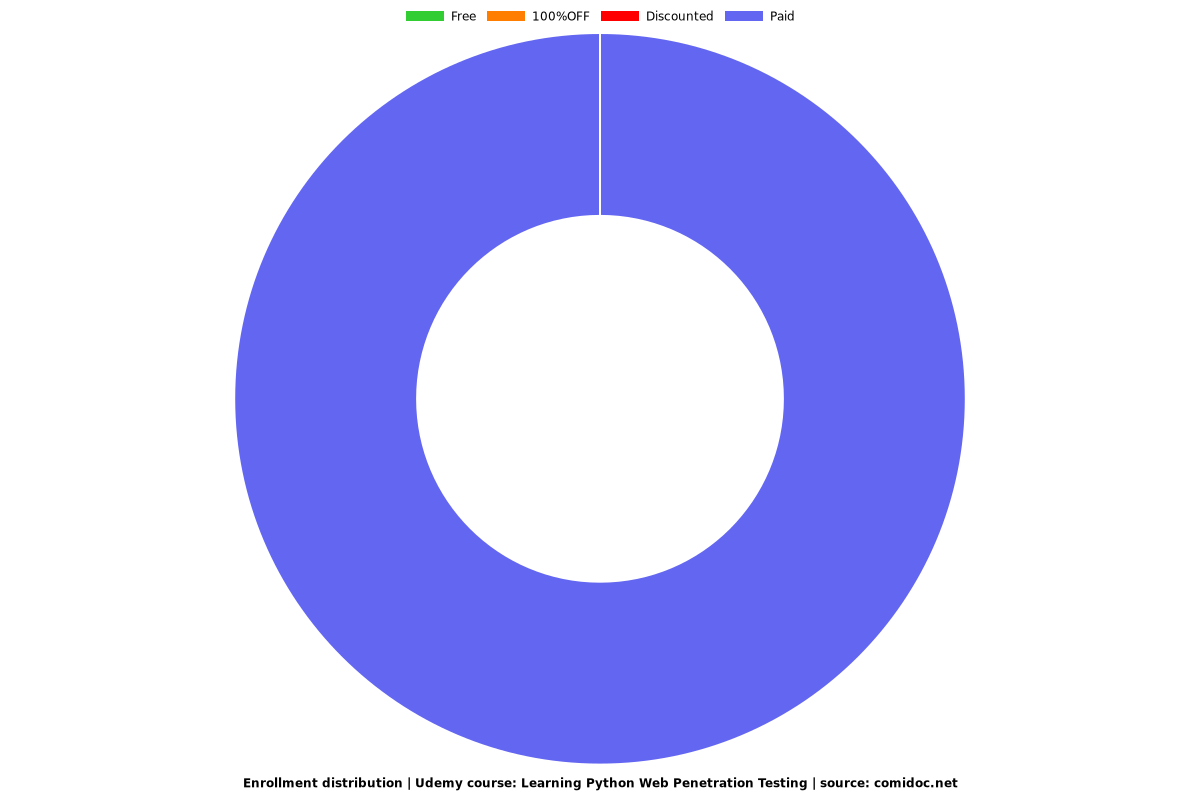
Enrollment distribution