Black Hat Approach to Hacking
Learn how a hacker hacks into the system and learn how to secure them from getting hacked.

What you will learn
Installing and updating Kali machine
Finding SQL Vulnerabilities
Password Cracking
Network Hacking
Wifi Hacking
Setting up and configuring Metasploitable server
Social Engineering
Exploring vulnerability with Kali
Digital Forensics
Why take this course?
The Black Hat Approach to Hacking is a Computer skilled professional course where you learn all the basics of ethical hacking and countermeasures respectively.
Learn the fundamentals of Ethical Hacking by enrolling in the Black Hat Approach to Hacking course. It helps you fully comprehend the technique by touching upon each and every concept in a detailed manner through the comprehensive modules designed by industry experts. By mastering the materials provided, you will gain the confidence to pursue the field on your own. Enroll in this course and get your Ethical Hacking certificate to gain the profound capabilities and skills needed to make your mark in the real-world.
This course is for you if:
You are a beginner wanting to learn about Ethical Hacking.
You are an IT professional aspiring to understand Cyber Crimes.
You are a web application penetration tester.
You are an entrepreneur who wants to master information security.
Content
Introduction
Installing Virtual Machine (Kali Linux)
Setting up Server
Information Gathering
Social Engineering
Network Security
Digital Forensics
Password Cracking
Reviews
Coupons
| Submit by | Date | Coupon Code | Discount | Emitted/Used | Status |
|---|---|---|---|---|---|
| - | 10/9/2019 | PROMOTIONS | 100% OFF | 50/18 | expired |
| - | 1/15/2020 | HACK_ME | 100% OFF | expired |
Charts
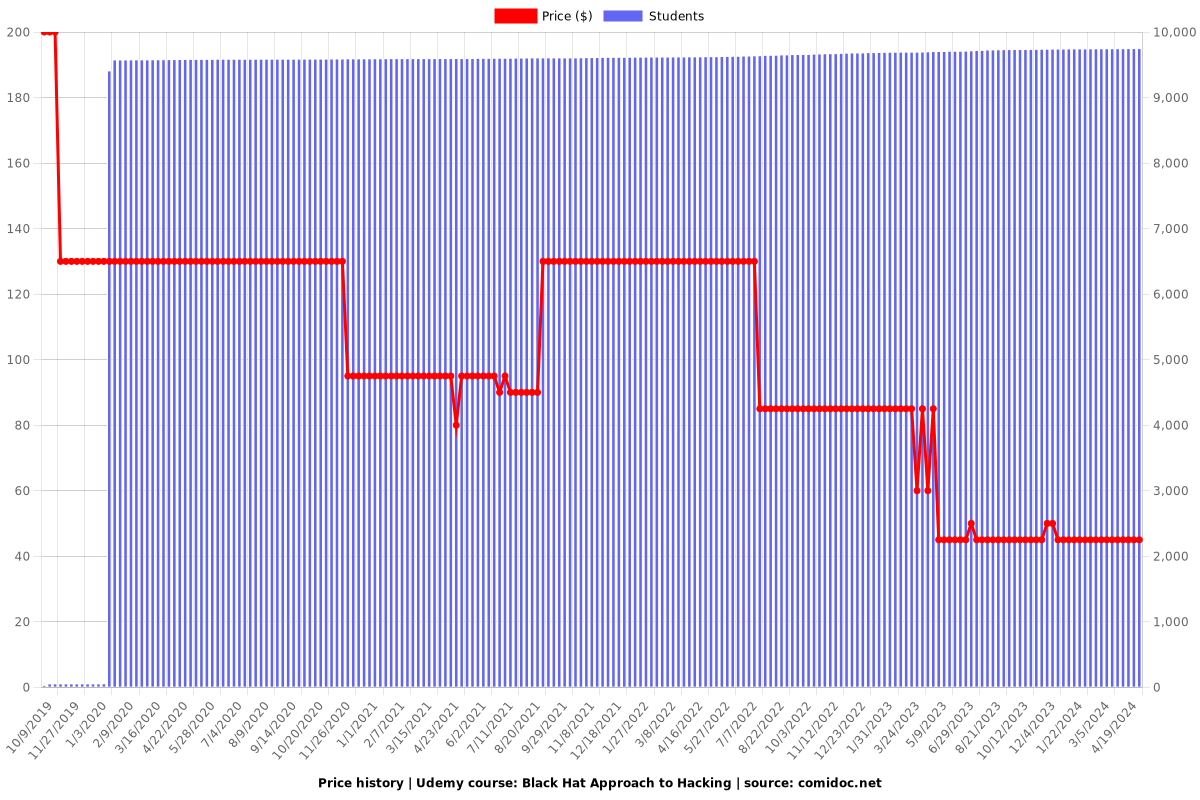
Price
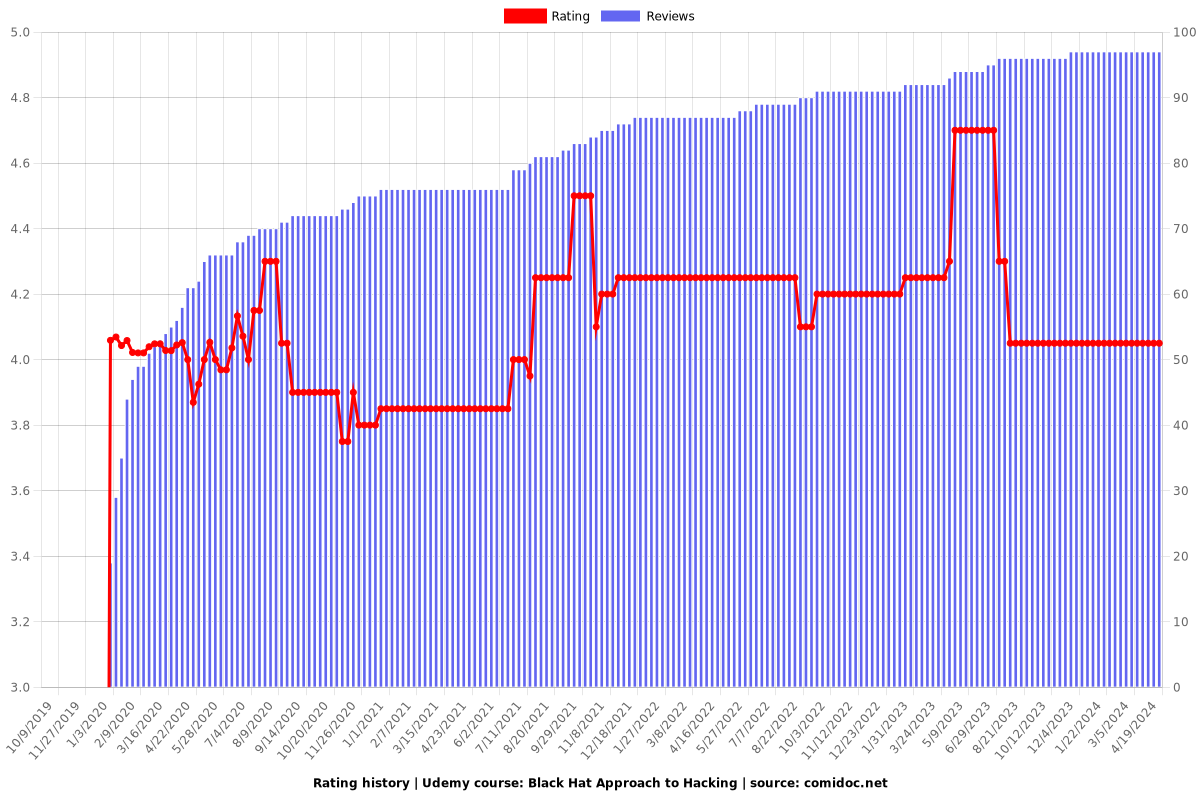
Rating
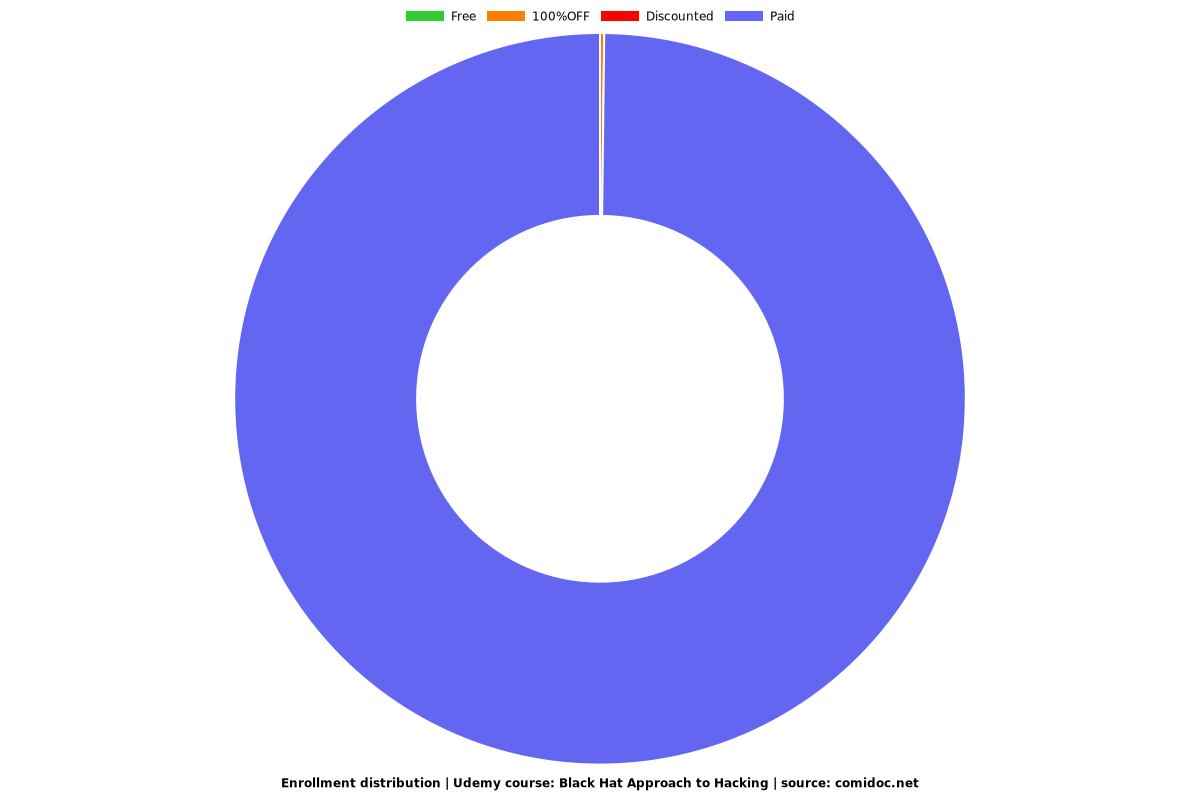
Enrollment distribution