Cyber Security's Frontier: Emerging Trends and Technologies
A Comprehensive Exploration of the Latest Advancements Defending the Digital Landscape
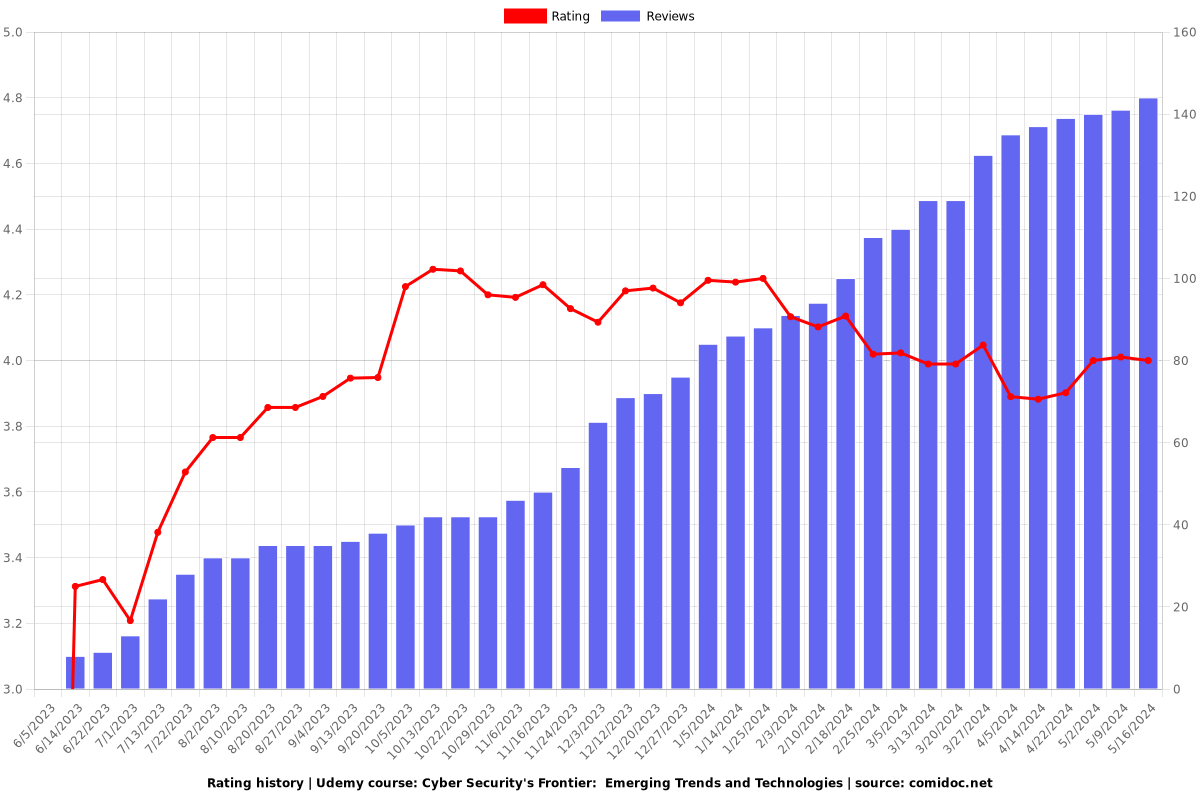
4.00 (144 reviews)

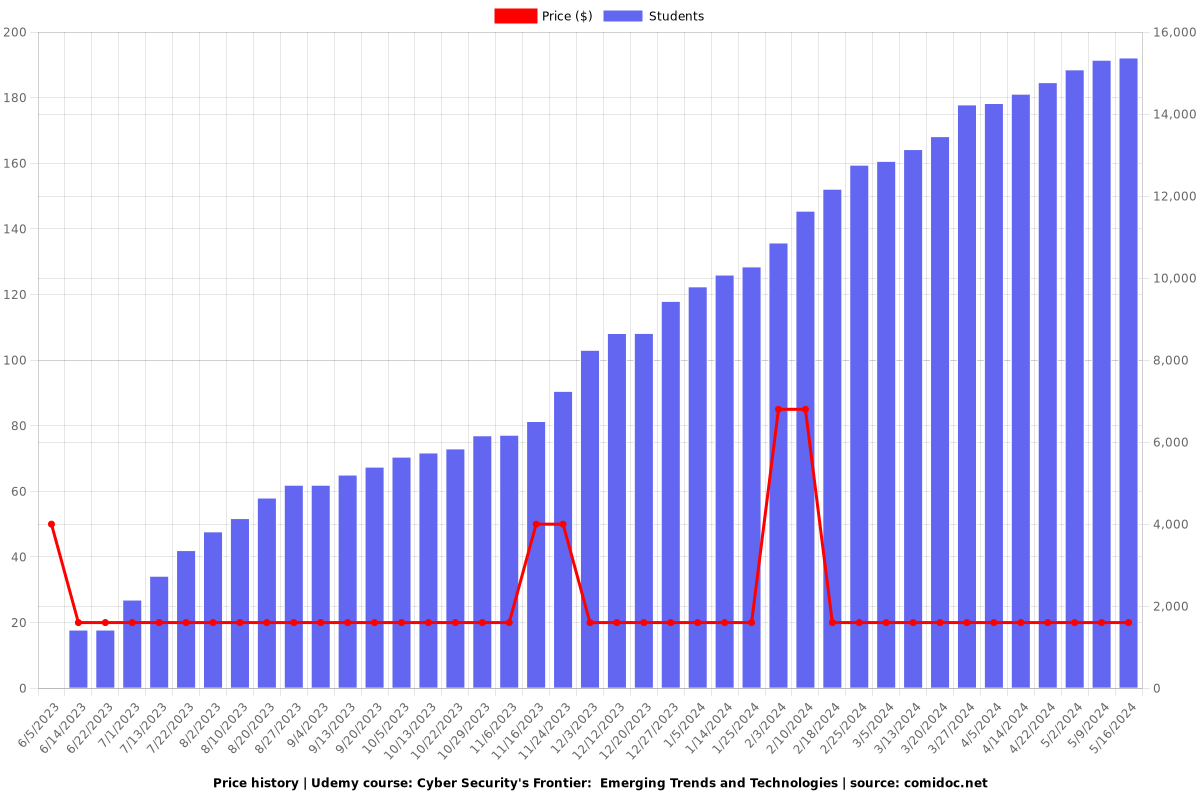
15,371
students
1 hour
content
Oct 2023
last update
$19.99
regular price
What you will learn
The students will learn about emerging cybersecurity threats such as ransomware, social engineering and zero-day flaw.
The students will understand the need to stay updated with latest developments and ideas in the field of cybersecurity.
The students will understand the importance of privacy and data protection in the digital age.
The students will also learn about cutting-edge technologies ( AI, blockchain technology, IoT etc.,) that are transforming the cybersecurity domain.
Why take this course?
🛡️ **Cyber Security's Frontier: Emerging Trends and Technologies** 🚀
---
### **Introduction to the Digital Defense Landscape**
In the wake of the global shift towards remote work following the 2020 pandemic, our digital defense mechanisms have been put to the test. As more individuals operate from home, cyber security has become a critical concern, with attackers seizing the opportunity to exploit vulnerabilities in this new, expanded digital landscape.
---
### **Understanding Cyber Threats**
- **Targeted Ransomware Attacks**: These are sophisticated attacks where cyber criminals specifically target organizations or individuals to demand a ransom in exchange for access to encrypted data.
- **Zero-day Flaws**: A zero-day flaw is a vulnerability that developers are unaware of until it is exploited. The moment this flaw becomes known to the public, the race is on to patch it before it's abused.
- **Social Engineering & Spear Phishing**: These deceptive techniques manipulate users into divulging confidential information by impersonating trusted entities or individuals. The goal? To access sensitive data or systems.
- **Insider Threats**: With the rise of insider threats, it's clear that the risks come from within organizational walls, often through negligence, disgruntlement, or intentional malice.
---
### **The Cybersecurity Ecosystem**
As we delve deeper into cyber security's frontier, we explore the following:
- **Cloud Security**: The cloud has become an attractive target for cybercriminals due to its vast amounts of data and the interconnected nature of services.
- **Top Cloud Threats**: Organizations must navigate a range of threats, from data breaches to insecure APIs and account hijacking.
- **Internet of Things (IoT)**: The proliferation of IoT devices introduces an array of potential vulnerabilities, as each connected device can serve as a point of entry for attackers.
---
### **The Demand for Cybersecurity Professionals**
The demand for cyber security professionals is skyrocketing due to the ever-evolving nature of digital threats and the complexity of defending against them.
---
### **Innovative Solutions in Cybersecurity**
- **Cyber Insurance**: While not a panacea, cyber insurance can help mitigate financial losses from cyber incidents, but it's not a replacement for robust security measures.
- **Zero Trust Architecture**: This approach mandates strict identity verification for every person and device attempting to interact with networks, ensuring that users have the least amount of access necessary.
- **Mobile Security**: With the increase in mobile device usage, these are becoming prime targets for cybercriminals, necessitating more secure mobile environments.
- **Bring Your Own Device (BYOD)**: The BYOD trend introduces new risks as personal and work data can become intertwined, requiring stringent policies and technologies to protect sensitive information.
---
### **Emerging Technologies in Cybersecurity**
- **Artificial Intelligence (AI)**: AI is revolutionizing cybersecurity by automating threat detection and response, making it possible to analyze vast amounts of data for irregular patterns at an unprecedented scale.
- **Blockchain**: The immutable ledger technology offers a new level of security and integrity in data storage and transmission.
- **DevSecOps**: This approach integrates security practices at every stage of software development, operation, and maintenance, ensuring that security is a shared responsibility across teams.
- **Homomorphic Encryption**: An advanced encryption technique that allows computations to be carried out on ciphertexts without decrypting them first.
- **Post-Quantum Cryptography**: This field develops cryptographic algorithms believed to be secure against attacks by quantum computers.
- **Biometric Technologies**: These offer a more secure form of user authentication, leveraging unique physical characteristics to verify identities.
- **Endpoint Detection and Response (EDR)**: EDR solutions provide comprehensive visibility into what is happening across endpoints, offering an advanced level of threat detection and response capabilities.
---
### **Course Objectives**
This course aims to equip you with the knowledge to navigate the complex landscape of cyber security, understanding its emerging trends, technologies, and threats. By exploring these topics in depth, you'll gain insights into how to protect sensitive data and defend against the ever-evolving digital attacks that threaten our digital frontier.
Join us on this journey to the cutting edge of cyber security, where each step you take will fortify your digital defenses and prepare you for the challenges of tomorrow. 🛡️
---
### **Conclusion**
In conclusion, cyber security is a dynamic, evolving field that demands constant vigilance and adaptation. As technology advances, so too do the methods used to protect it. This course will provide you with the tools and knowledge necessary to stay ahead of threats and safeguard the digital future. Enroll now and become a guardian of cyberspace's frontier! 🌐🚀
Reviews
Galadima
December 29, 2023
Taking the course has given me more understanding on the importance as to why both individuals and organizations need to know more about Cyber Security. The world is going digital, and so does criminal activities.
Kushal
December 21, 2023
The presenter is only reading the slides. Also very difficult to maintain concentration with the presenter moving around continuously and the text moving in the front and behind the presenter. Not sure, why this course is highly rated. Good to enroll if you get it for free, but not worth purchasing.
Zia
November 27, 2023
well the instructor's effort was good but lacking examples makes the contents difficult to understand and behave just like cramping something.
Charts
Price
Rating
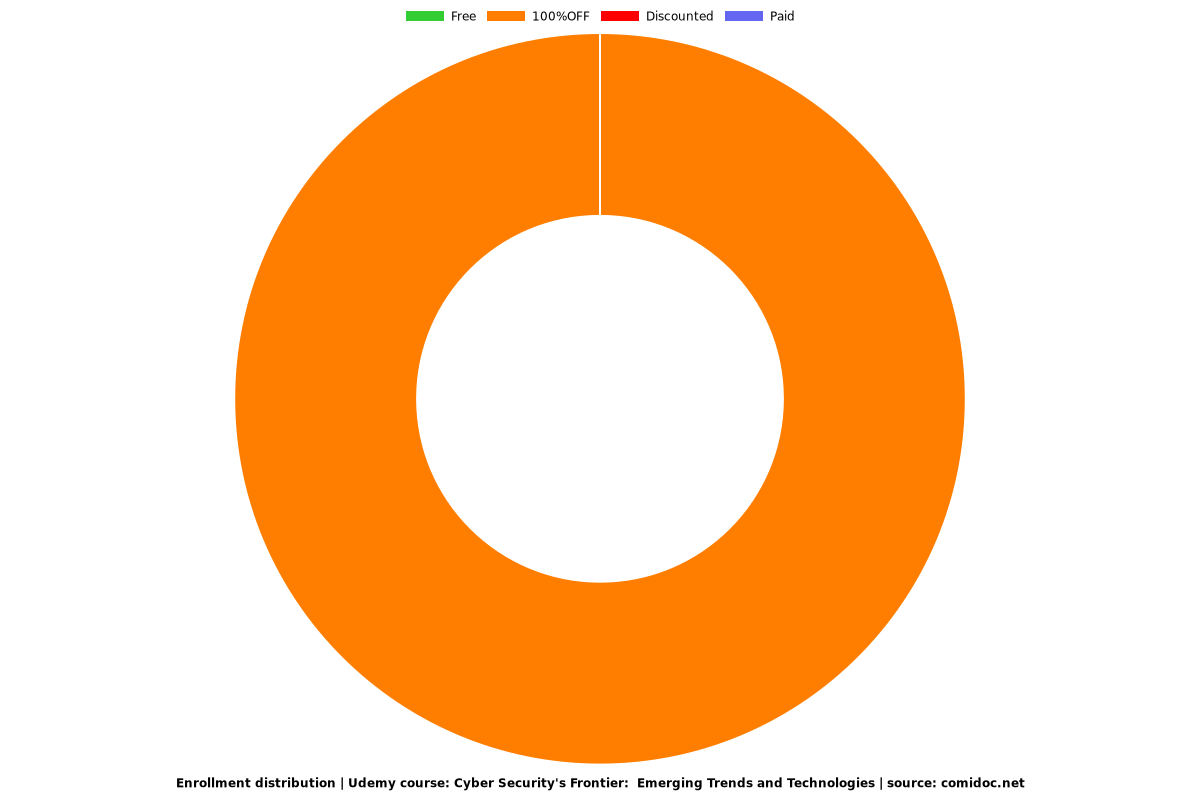
Enrollment distribution
5367198
udemy ID
6/5/2023
course created date
6/5/2023
course indexed date
Prabh Kirpa Classes
course submited by